Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.
Build A Zero Trust Model by First Killing Local Admin Rights
Words mean something. The words we use change over time, reflecting the transitory nature of our notions and thoughts at large. For thirty years, we embraced the concept of networking as a way to “share” things. Sharing reflects openness and requires a sense of trust.
Currently, one of the dominating catchphrases is “zero trust.” A Zero Trust model implies that we trust no one. This dramatic shift manifests the dichotomy we face today in a world that is digitally transforming itself and also under constant attack.
How do we share ideas among our peers and partners while trusting no one?
How we came to the model of zero trust
So what changed over the course of thirty years? A whole lot! While we still use the concept of LAN to describe the topology of our corporate networks, in reality, the typical enterprise today is a mesh topology. Today’s network is a vague collective assortment of BYOB devices, corporate partners, smart HVAC controls, IoT sensors and that vast collective pool we call the cloud. Attack surfaces are ever-expanding, and they are no longer defined by a hard perimeter. Networks have also grown in complexity, complicating the security process further.

A primary influence triggering this evolutionary mindset is money. Cybercrime now costs the global economy $2.9 million per minute. That equates to $1.5 trillion dollars annually. To thwart these costs, Gartner estimates that the world spent $1.24 billion on cybersecurity in 2019, an 8.7 percent increase over the prior year. Yet, despite the financing of this global effort to bolster cybersecurity, the bad guys continue to win.
Despite all the attention to stop ransomware in recent years, file encryption attacks surged 77 percent to 46 million attacks in 2019. In fact, half of all malicious emails in 2019 contained ransomware. Simultaneously, data breaches increased by 54 percent in 2019. How can this happen in an era in which nearly every enterprise utilizes some sort of robust firewall to fortify their perimeter while utilizing antivirus protection and spam filtering to protect users and desktops?
What does a Zero Trust Model mean?
Thus, we arrive at our current state in which the mantra, a zero trust model, is becoming a rallying cry throughout the cybersecurity industry. But what does a zero trust model really mean? We should not accept the term in its literal meaning. Trusting absolutely nothing within your network environment is simply not pragmatically possible. An absolute zero trust model would require terminating all network connectivity plus shutting off all the computers and going back to pencil and paper.
The model of zero trust pertains to the outdated concept of security based on hard boundaries. In the same way that the French nation found that their highly fortified Maginot line did little to stop the blitzkrieg forces of German panzer divisions in World War II, the concept that a secured border can adequately protect your enterprise is simply no longer true. The enemy is no longer permanently located outside the firewall perimeter. The enemy may just as likely be within your network. Last year, hackers lurked within the network of Citrix Systems for six months, until the FBI discovered the breach and contacted company management.
The concept of least privilege
Even the word “hacker” is an outdated metaphor today. Attackers no longer hack through complex firewall perimeters—they take the easy way, such as coaxing an unsuspecting user to initiate a malware infection through a phishing attack or file download. Often they simply log in through the front door with compromised credentials. This is why the concept of least privilege is so imperative today. Zero trust models mean that you can no longer allow users unrestrained privilege or rights on their devices:
Complacency can no longer be tolerated. Enterprise security is a moving target. We cannot assume that the strategies and solutions that effectively protected us yesterday will work tomorrow. Traffic originating from within our own networks must be addressed with the same level of skepticism that we enforce towards Internet traffic.
How PolicyPak fits into the Zero Trust Model
Just as there rarely is a smoking gun to identify an attack, there is no single security solution to fully protect you. Organizations must approach cybersecurity with a strategy of Defense in Depth (DiD) in which a series of security mechanisms operate in redundant fashion to increase the security of the network as a whole. This multilayer strategy addresses the numerous attack vectors that today’s typical enterprises are exposed to, as well as ones that are as of yet unknown.
At PolicyPak, we create tools to help companies and organizations contend with a zero-trust world. While PolicyPak cannot aid you in every required facet of network security such as network segmentation, data encryption or traffic analysis, our solutions give you the admin powers to lock down, control and protect all your Windows devices, as well as their users.
TRY POLICYPAK FREE »
Let’s start with PolicyPak Least Privilege Manager. A zero-trust environment means that you cannot assume that your users are the ones logging on. This means you cannot allocate local admin rights to them, lest you turn around and find that the users’ credentials are used against you. Additionally, you cannot trust that they will practice good cyber hygiene by not wantonly or inadvertently clicking on things they should not. PolicyPak Least Privilege Manager lets you limit and strictly enforce the access and privilege of your users while ensuring that they can still easily perform all their required tasks.
There are two main aspects to PolicyPak Least Privilege Manager. The first is SecureRun™, which simply blocks all items that are not “properly installed” by the admin. In other words, unless a known admin account installed it, it cannot be trusted. Every time a user clicks on an executable, MSI, script or Java .JAR file, SecureRunTM, check to see who owns it. When a user downloads a file off the Internet or copies it from a USB, they own it. This fact is shown in the screenshot below.
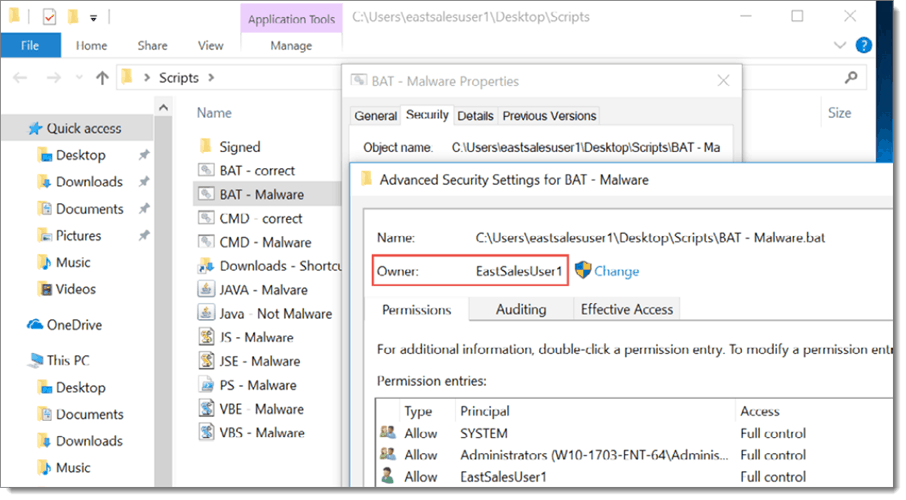
If the owner is not a member of the defined list of installers, access is instantly denied. An example of the default SecureRunTM is shown below.
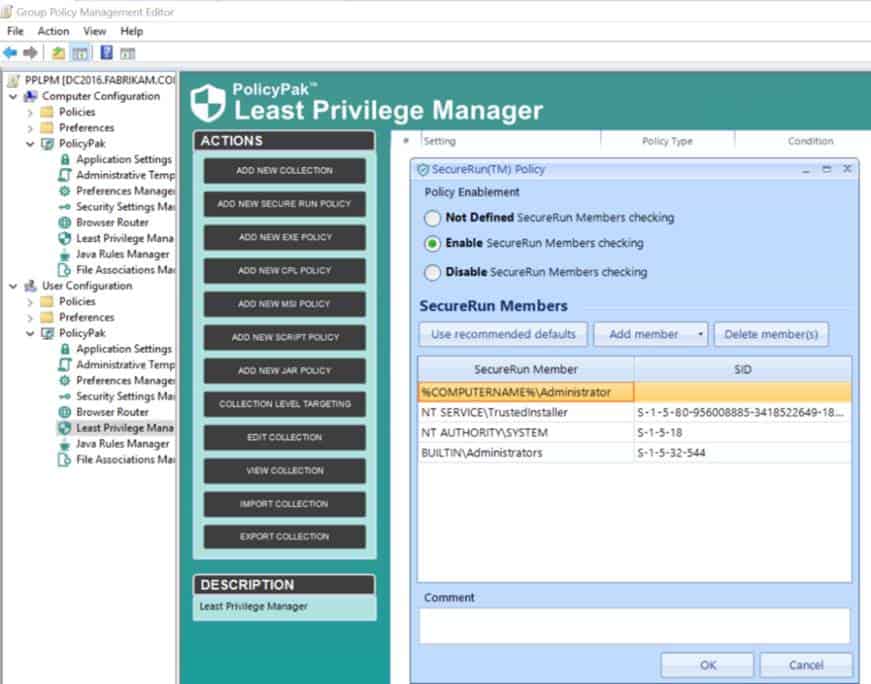
The result is that you can enforce a zero trust model: When the correct people have installed the application, the application runs. When the incorrect people have attempted something they should not, the application blocks it.

As stated earlier, an absolute zero trust model is simply not practical. Users sometimes need to have incremental privileges and access to things such as Control Panel applets or network card settings. They may need to install an MSI application, install a printer or bypass a UAC prompt.
PolicyPak Least Privilege Manager gives you the ability to assign granular privileges, such as these, to give a user just enough access to perform a designated task but no more than they need to get the job done.

To see a video demonstration on how to let standard users install MSI applications without admin rights, watch below:
You can also watch below for a demonstration of how standard users can overcome those annoying, but necessary UAC prompts without admin privileges.
One of today’s realities is that your organization likely does not have the manpower to completely protect your users and devices. You need the aid of software-based protection to provide blanket protection and granular protection of your desktops and installed applications.
In an on-prem world, many companies rely on traditional Group Policy to manage and deliver Windows configuration settings. If that’s your organization, then PolicyPak is ready for you with PolicyPak Group Policy Edition.
Some companies are transitioning to the cloud for lower costs and greater agility and security. Ironically, MDM solutions do not provide anywhere near the setting coverage of standard Group Policy. In this case, PolicyPak is ready for you with PolicyPak MDM Edition. In addition to all the PolicyPak security settings, the MDM Edition also enables Windows administrators to deploy the full gamut of 10,000+ real Group Policy and Group Policy Preferences configuration settings to all Windows devices. This includes MDM-enrolled computers or offsite non-domain joined machines.
SIGN UP FOR A POLICYPAK WEBINAR »
You can also provide a zero trust model within PolicyPak Application Manager and PolicyPak Java Rules Manager.
PolicyPak Application Settings Manager enables you to dictate IT settings for over 500 common desktop applications that Group Policy never covered. PolicyPak Java Rules Manager enables you to whitelist only Java-based websites and marry them to a version of Java that you trust.
PolicyPak gives you the security and control you need in a zero-trust world while ensuring the user functionality you need in a competitive business world. Ensuring required functionality and zero-trust protection may be a tall order in today’s ubiquitous threat environment, but PolicyPak achieves that for its customers.


