Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.

Ransomware is Once Again the Method of Preference for Cybercriminals
In 2016 the FBI proclaimed ransomware a billion-dollar industry. Ransomware dominated headlines around the world as companies, healthcare centers and governments found themselves combating the digital plague that encrypted data and brought down networks.
According to the Verizon 2017 Data Breach Investigation Report, one in three malware attacks were ransomware related in 2016. The onslaught of attacks culminated in the summer of 2017 when the WannaCry and NotPetya outbreaks swept the globe, disrupting essential operations and services for weeks for many global organizations. Within the cybersecurity space, ransomware was considered the #1 cybersecurity threat during that period and, at the time, it seemed as though the wrath of ransomware knew no bounds.
And then, ransomware languished somewhat as cryptojacking began its ascension onto the global malware stage. Thanks to the cryptocurrency craze, ignited by the skyrocketing appreciation of Bitcoin, cryptomining malware attacks increased by 8,500 percent in the last quarter of 2017. Cryptojacking soon overtook ransomware as the top malware threat, with McAfee proclaiming that “Ransomware is rapidly vanishing”, and cryptocurrency mining is starting to take its place.” By the fourth quarter of 2017, ransomware had even dropped out of the top five malware threats.
While the number of reported malware attacks dropped considerably, the underlying data showed that ransomware was down but not out, as it still made up 64 percent of all malicious emails in the third quarter of 2017. Then, in the early months of 2018, it became clear that the hibernation of ransomware was only short lived. In March, the City of Atlanta had several key government services disrupted after a city employee downloaded the SamSam ransomware variant by clicking on an embedded email link. Some critical services were down for over a week and the estimated cost to address the issue is upwards of $17 million. And just a week prior, the Colorado Department of Transportation was hit by a similar attack, decommissioning nearly all of its 2,000 computers. And as if once wasn’t enough, weeks after working around the clock to restore services, the department was struck by the malware variant yet again.
Ransomware returns with a vengeance
It was obvious that ransomware wasn’t going to take the summer off (or the fall, for that matter), as there were a string of high profile attacks, including:
- Global shipping giant Cosco Shipping Lines shut down operations at several port locations throughout North, Central and South America after ransomware impacted email and network telephone operations in those areas.
- A mattress retailer in Winnipeg, Canada paid a hacker a ransom of $2,000 after an attack debilitated its servers, halting operations completely.
- Government employees at the Alaska Borough of Matanuska-Susitna found themselves resorting to typewriters, stamping books and hand writing documentation when the network of the government municipality was shut down by ransomware.
- The Bristol Airport was attacked on September 14, forcing airport employees to post flight arrival and departure schedules on posters and whiteboards as the attack halted internal communication throughout the airport.
With so many recent attacks, it comes as no surprise that Malwarebytes announced that ransomware attacks are once again the preferred method of crypto hackers and cybercriminals, making it an active threat to your enterprise. And in reality, the threat credibility of malware never really subsided, as it is now believed that the reduction in attacks was due only to hackers focusing their efforts on enterprises rather than consumer users.
So how do you protect against malware and malicious code from infiltrating your enterprise devices?
As a first step, you can employ a blacklisting or whitelisting strategy, though the time required to manage that can be exhausting for administrators who already have limited bandwidth.
Fortunately, there is another way – PolicyPak SecureRun. Part of PolicyPak Least Privilege Manager, SecureRun ensures that applications are only permitted to run when “properly installed” or otherwise sanctioned by the administrator. What’s more, it doesn’t require any documentation or additional work, because it is automated. Whatever the reason for the fluctuation in attacks, it is of little concern to PolicyPak customers, because with SecureRun they are, and will continue to be, protected from ransomware.
How Secure is SecureRun?
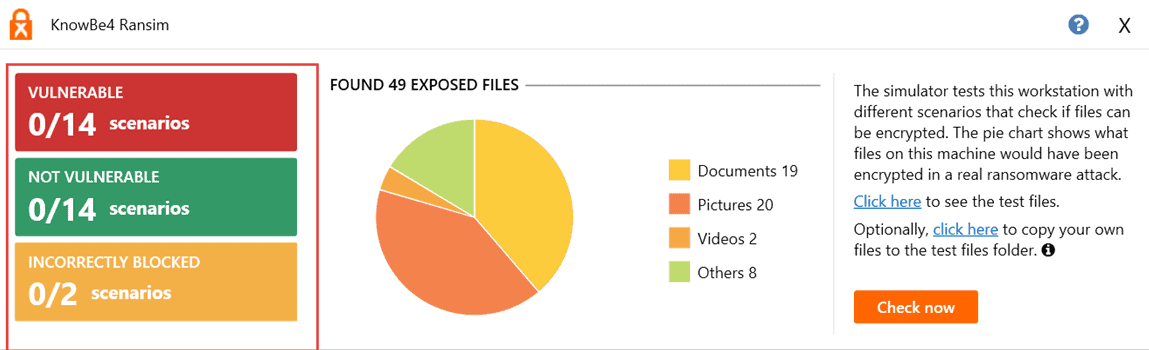
Recently, we conducted a test to assess the potential vulnerability to ransomware attacks for computers protected by PolicyPak SecureRun. To do this, we used KnowBe4’s Ransomware Simulator called RanSim which simulates 13 common ransomware infection scenarios, as well as one cryptomining infection scenario to measure the vulnerability of these attacks for a designated machine.
The comparative results were absolutely definitive. The test administrator first used a Windows 10 machine to define the “beforehand” vulnerability of the machine. According to RanSim, the machine was vulnerable to every one of the 14 scenarios as is shown below.
PolicyPak SecureRun was then setup and configured on the machine and another simulation was run. The end result was zero vulnerabilities.
A hacker only needs one device to compromise your network. You, on the other hand, have to protect all of your devices. Don’t make the task any more difficult than it has to be. Harden all of your Windows devices with PolicyPak SecureRun and let other people worry about ransomware and other malicious types of malware.