WinZip is on all your desktops and all your users use it. So how are you going to manage its critical settings
- Enforce password requirements
- Remove “Cameras” tab ability
- Set up Explorer Context Items
- Enforce where users Save, Extract, and store temp files
… and just about every other WinZip setting?
WinZip itself has no native Group Policy support with ADM or ADMX files to control these key settings, so what are you going to do? Watch this video to find out:
The best part is all the “PolicyPak superpowers” you just learned about in this video (showing WinZip as an example) are also available for tons of OTHER applications – including ones you might be deploying in house or have custom made.
Our solution isn’t a mere “ADM” template, it’s a true Group Policy extension, with powerful management and lockdown capabilities. PolicyPak can deliver, lockdown and revoke critical settings – the way you need to using Group Policy.
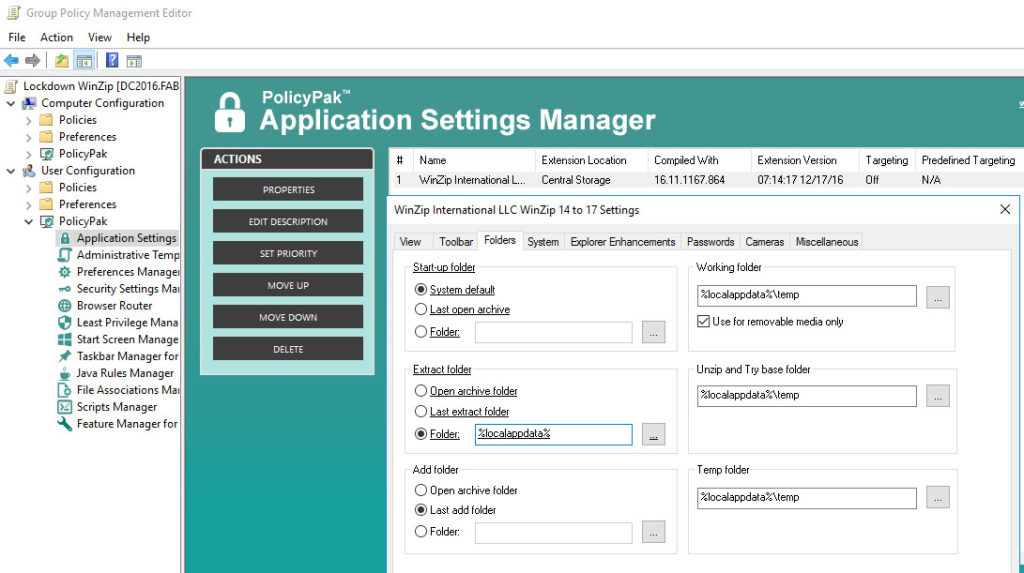
With PolicyPak and the free Pre-Configured PolicyPak for WinZip, you get full control over WinZip using Group Policy. True granular control for each OU or user – using normal Group Policy controls.
Doesn’t this seem like the right way to manage your desktop applications in your enterprise and Windows 7 and Windows XP?
Again, once you’re using PolicyPak to manage WinZip, you’ll also be able to manage all your other enterprise desktop applications the same way:Firefox, Java, Acrobat, and any custom application you have. They’re 100% included – absolutely free. It’s all included when you’re a PolicyPak Professional customer.
PolicyPak was designed by Microsoft MVP, Enterprise Mobility Jeremy Moskowitz – who “wrote the book” on Group Policy, runs GPanswers.com, and lives and breathes Group Policy and enterprise software deployments and desktop lockdown.
When you’re ready to get serious about managing WinZip today PolicyPak is ready for you today, and for all applications you want to manage and lockdown in the future.
Manage WinZip with Group Policy video transcript
Hi, this is Jeremy Moskowitz, and in this presentation we’re going to cover PolicyPak’s superpowers a little bit slower than we did in the quick demonstration. We have a lot of great stuff to cover, so let’s go ahead and get started. We’re going to cover Enforcement, Reversion, AppLock, Offline Mode and Switch Mode – all of our major superpowers. Let’s go ahead and take a look at all of them.
To get started, I’m going to assume you have a PolicyPak created. We have other videos to show you how to do that. You can see here, I’ve got a GPO called “Control WinZip.” I’m modifying that GPO here. I’m going to go to “PolicyPak/Applications/New/Application” and select “PolicyPak for Winzip14.” Here you can see it looks exactly like the application.
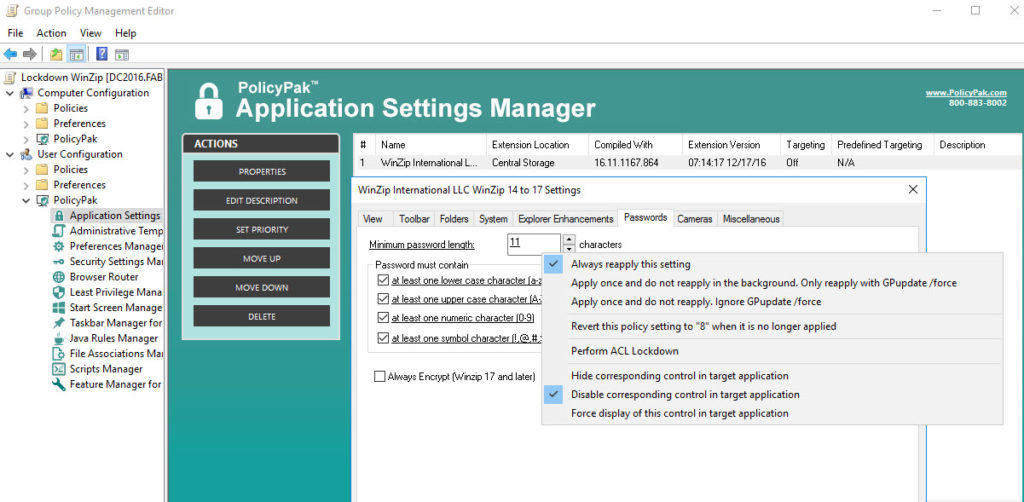
Let’s talk first about our Enforcement modes. If I wanted to drive down all of these particular settings, this is our default to “Always reapply this setting.” That will take effect any time the Group Policy background refresh takes effect, which is about every 90 minutes or so, or when a user logs off and logs back on.
We also have some other superpowers in the Enforcement zone as well. We can “Apply once and do not reapply in the background. Only reapply with GPUpdate /force.” If we wanted to, we could deploy it once. But if we really wanted to get it back, we could rerun the GPUpdate /force on a target machine.
We could also make it a true preference, which is we could deploy it once with “Apply once and do not reapply. Ignore GPUpdate/force” and it would never reapply it ever again. But I like the first one, “Always reapply this setting.” If we’re thinking it’s important, we always want to effect it.
So that is Enforcement. For Reversion, we could “Revert this policy setting to the default value when it is no longer applied.” We can see that we’re applying the checkbox. If the policy doesn’t apply anymore, should we leave the checkbox there? Well, you can if you want to, or you can “Revert this policy setting to the default value when it is no longer applied.” I’m going to do that for these first two, and only these first two.
Then for these other two guys, let’s talk about our AppLock modes. For AppLock, we can “Hide corresponding control in target application.” That’s going to literally remove it so it’s not available. Let’s go ahead and do that for this third one here. For this fourth one, we’re going to “Disable corresponding control in target application.” So we’re going to gray it out. And my favorite, let’s say we have got “Cameras” here, we can right click here and “Hide whole tab from target application.” Those are our AppLock enforcement modes.
Let’s go ahead and click “OK.” Let’s go over to our client machine. We’ll do a quick GPUpdate here, and let’s see what happens. OK, now that that’s done, we’ll rerun “WinZip” here. Go over to “Options/Configuration…”
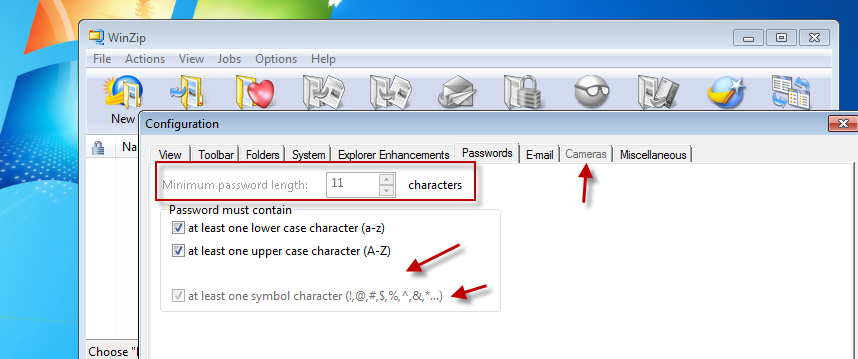
Let’s head on over to “Passwords.” Hey, look at that. We’ve configured these first two settings. We said it’s always going to reapply. We’ve literally removed the UI from the third element, and we’ve grayed out the fourth element. That’s exactly what we wanted. Remember “Cameras”? Well, “Cameras” is gone. We’ve eliminated “Cameras.” They can’t manipulate that.
Let’s see what happens if a user unchecks these checkboxes and then the Group Policy Update reoccurs. If we rerun GPUpdate, let’s see what happens. As soon as that’s done, we just go back to “Options/Configuration…” It puts it right back. So that gives you an incredible amount of control to guarantee your settings.
Now let’s see what happens if a user falls out of scope of management of this Group Policy Object, or the GPO no longer applies. Let’s go ahead and close out WinZip here. Go back to our GPO here. We’ll minimize this. To make this demo go quick, we’ll right click over the GPO link and uncheck “Link Enabled.” Now it’s grayed out. It’s no longer affecting my “East Sales Users.”
So let’s see what happens if I run GPUpdate on the client machine. Now that that’s done, the settings we said should revert back, will.Let’s find out. “Passwords” revert back. We only told the first two settings to revert back. We decided to leave these other two settings alone when the policy no longer applies. You notice how the AppLock features peel away? And, of course, the “Cameras” node is back.
So we work exactly the way you would expect with Group Policy. We also have some extra superpowers when it comes to offline enforcement. Let’s go back over to the GPO here, right click and select “Link Enabled.” As you would expect, the next time we run WinZip after getting the latest Group Policy settings we will be enforced again. That’s, of course, what you would expect. And, of course, we come right back, affect the “Passwords” settings, remove the “Cameras” tab. Everything’s great.
But what happens if we’re offline? If we’re offline, in order to do this little demonstration, I’m going to uncheck the network cables using my virtualization tool. I’m going to “Disconnect” the network cables here, and you’ll see that my Windows 7 machine reacts here. If I’m a user and I’m in WinZip and I decide I’m going to try to be a bad guy and work around these settings, I click “OK.” I try to work around these settings.
What happens the next time Group Policy Update occurs? Well, the next time Group Policy Update occurs, you’re going to get an error message from Windows 7. The reason is that it can’t make contact with a domain controller. Well, in that case, we still have you covered. So even though WinZip didn’t get updated on a GPUpdate, we’ve got our extra superpower waiting to happen.
All you need to do is have your user log off or log back on. Let’s go ahead and see that real quick. When they log off and log back on, even though we’re offline, we’ve automatically cached our settings locally and we guarantee them to come back the next time they log on just like that.
If that’s not good enough, if you want even more fine grain control, if they uncheck the checkboxes here, we give you a scriptable command line tool called “ppupdate.” So instead of GPUpdate, we give you PPUpdate. It runs just that fast. Go to “Options/Configuration…” It puts back in those settings. So even if your users are offline, we guarantee those settings to come down the next time they log on. Or you can script those settings to come back down with the PPUpdate utility that we provide.
The next thing I want to demonstrate is called Switch Mode. Switch Mode can enable you to deliver a user side setting to any user on a particular desktop. What we’re going to do is “Create a GPO” here. We’ll call this “Winzip for all users on these machines.” This is very specific. Before you saw me drive user side settings to the user. Now I’m going to do something special by driving user side settings into the computer.
Here’s “PolicyPak/Applications” on the computer side. We’ll go to “New/Application” for “PolicyPak for Winzip14.” If we want it to specify these two settings here for “Passwords,” that’s great. These are user side settings, but we’re going to do something special and drive them into any user who is on these particular computers.
Let’s take a look at that. What I’ve done in advance is I’ve moved one particular desktop called “WIN7COMPUTER-64” into the “East Sales Desktops.” That’s right here. Now all I’m going to do is log on as some user, it doesn’t matter what user it is. I’ll log on as “westsalesusers.” Even though this particular GPO isn’t affecting the user, it’s only affecting the computer,every user upon this computer will get the exact same setting.
All we need to do is run the application. In this case, the application’s virtualized. We don’t make any particular distinction there. Then if we go to “Options/Configuration…,” go over to “Passwords,” every user who is on this machine will get these particular user side settings.
So that is Enforcement, Reversion, AppLock, Offline Mode and Switch Mode – all of the PolicyPak superpowers. I hope you enjoyed this video, and I hope you’ll watch the next one.
Thanks so much. Bye-bye.