Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.

Achieve ACSC Essential Eight Risk Mitigation with PolicyPak
The ACSC Essential Eight Maturity model was developed by the Australian Cyber Security Center (ACSC) in an effort to fight against cybercriminals and malicious malware. The ACSC developed a series of prioritized mitigation strategies, called the ACSC Essential Eight Maturity Model, to help organizations mitigate the severity of security incidents by various cyber threats. These threats include both targeted cyber intrusions and persistent threats of external adversaries and malicious insiders that steal or destroy data. It also targets ransomware and other malicious code threats that can destroy or prevent the functionality of networks.
The Essential Eight
For Marvel comic enthusiasts, there is the Fantastic 4. For cybersecurity professionals, there is the Essential 8. The ACSC Essential Eight Maturity Model is a document created by the ACSC the outlines eight security baselines to combat today’s most consistent and prevalent cyberthreats. These eight security strategies are geared towards hardening security and protecting workstations and servers. In order to assist organizations in implementing the eight baseline strategies, the ACSC has aligned the Essential Eight strategies with three different maturity levels. The objective for any organization should be to reach Maturity Level Three for each mitigation strategy. For some organizations, this may not be possible, in which case they must demonstrate a recognized level of due diligence or duty of care in order to satisfy compliance auditors or litigators. The three maturity levels are outlined as follows:
- Maturity Level One: Partly aligned with the intent of the mitigation strategy
- Maturity Level Two: Mostly aligned with the intent of the mitigation strategy
- Maturity Level Three: Fully aligned with the intent of the mitigation strategy
Achieve ACSC Essential Eight Risk Mitigation with PolicyPak
Two of the ACSC Essential Eight mitigation strategies are “Multi-factor authentication” and “Daily backups.” According to the ACSC, multi-factor authentication (MFA) should be utilized for anyone using a form of remote access to perform a privileged action or access a sensitive data repository. Remote access includes VPN, RDP, SSH, or another proprietary solution. The proper implementation of MFA makes it harder for adversaries to access sensitive information. Daily backups should be implemented to ensure that information and digital resources can be recovered following a cybersecurity incident. A daily backup strategy as outlined by the ACSC should involve the daily backup of any new or changed data, software, or configuration settings. Backups should be retained for one to three months (depending on the maturity level) in a non-writable or non-erasable manner.
The other six ASCS Essential Eight mitigation strategies are listed as follows:
- Application control
- Restrict administrative privileges
- Patch operating systems
- Configure Microsoft Office macro settings
- Patch applications
- User application hardening
We want to focus on these six, not because they are more essential than MFA or daily backups, but because you can implement these six security strategies using our PolicyPak solution suite. PolicyPak is a modern desktop management solution that empowers you to easily configure, deploy, and manage policies for both on-premise and remote environments. This includes security policies and protectionary configuration settings to ensure that your desktops remain secure and compliant. Let’s take a look at these other six mitigation strategies and how PolicyPak can help ensure you achieve Maturity Level Three for each of these.
ACSC Essential Eight: Application Control
The ACSC Essential Eight strategy of application control specifically refers to the practice “allow listing.” The application control mitigation strategy specifies that “allow listing” be implemented on all workstations to restrict the execution of executables, software libraries, scripts, and installers to an approved set. The same set of conditions is then required of all servers as well.
Allow lists are a highly effective way to ensure that users do not click or attempt to execute anything they aren’t supposed to. By implementing and maintaining an up-to-the-minute allow list policy, users are only able to launch members of an approved set. The problem with allow lists is the time-consuming task of maintaining them as new applications and scripts are constantly being introduced into the user environment. Fortunately, there is a far easier way to enforce your approved set—PolicyPak Least Privilege Manager.
PolicyPak Least Privilege Manager features a powerful tool called SecureRun™ that provides blanket level security protection to your desktops. Think of it as “allow listing” without the hassle. SecureRun™ was designed under the residing principle that when users introduce files onto their workstations by either downloading them off the Internet or copying them from a USB drive, they own the file. This concept is demonstrated by the following screenshot in Figure 1.

Figure 1: Users that introduce files will be considered the owner of the file.
When SecureRun™ is on, PolicyPak Least Privilege Manager checks to see who owns the file executable, MSI, script, or Java JAR file. SecureRun™ then maintains a list of who can initiate new processes. Below in Figure 2 is an example of the default list which you can modify to your needs.

Figure 2: Modify the SecureRun™ Member list to control who can initiate new processes.
A user not contained within the SecureRun™ Member list is not trusted, and processes originating from that user are blocked by PolicyPak Least Privilege Manager. The result is that properly installed applications can run perfectly well, but all unknown applications and scripts are blocked, as shown below in Figure 3.

Figure 3: Unknown applications and scripts are blocked by SecureRun™.
You can watch a video demonstration of how to enforce allow-listing policies to all of your Windows 10 machines using PolicyPak SecureRun™ on our website.
ACSC Essential Eight: Restrict Administrative Privileges
Enforcing the ACSC Essential Eight mitigation strategy of “Restricting administrative privileges” may be the easiest strategy of the set to comply with. All you have to do is deny standard users local admin rights to their machines. Mission accomplished! However, the problem lies in how users can get all of their work done in an environment that is void of granular privileges to things like running an executable, accessing a designated Control Panel applet, or overcoming UAC prompts. The objective after all is to stop cyber threats, not workflows.
That is where the magic comes in. PolicyPak Least Privilege Manager lets you create policies to run executables, install MSI applications, access Control Panel applets, or help online or offline users get past UAC prompts. The following screenshot in Figure 4 shows how you can give users access to privileged Control Panel applets. Notice that the policy creation process uses your existing Group Policy editor.
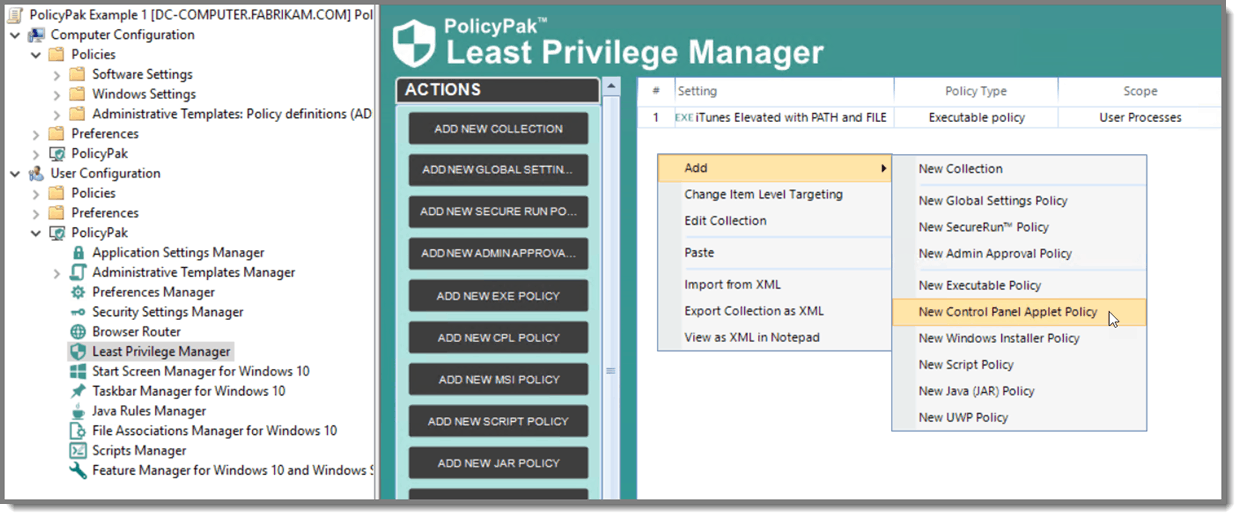
Figure 4: Creating a new Control Panel applet policy.
Then choose any Control Panel applet that your users will need, such as Device Manager (see Figure 5).

Figure 5: Selecting a Control Panel applet for a new policy.
With PolicyPak Least Privilege Manager, denying local admin rights to standard users isn’t only simple to implement, it’s easy to maintain as well. You can watch a video demonstration about how to kill local admin rights and run applications with least privilege on our website.
ACSC Essential Eight: Patch and Control Office Macros
Two more ACSC Essential Eight mitigation strategies are “Patch operating systems” and “Configure Microsoft Office macro settings.” The patching of operating systems pertains to security vulnerabilities assessed as an extreme risk. These vulnerabilities must be updated or mitigated within one month of a discovered vulnerability. Organizations should only allow Microsoft Office macros to be executed according to specific conditions that differ for each maturity level. They include:
- Allowing Microsoft Office macros to execute after prompting users for approval (Level 1)
- Allowing only signed Microsoft Office macros to be executed (Level 2)
- Allowing only macros from trusted locations to be executed (Level 3)
Ensuring compliance with both of these mitigation strategies is easily accomplished by Group Policy assuming all of your desktops operate in a simplistic on-prem AD environment. Unfortunately, the world is no longer that simple anymore. Many enterprises have a mixture of machines that are joined to AD, Azure, or nothing at all. Wouldn’t it be nice to deliver Group Policy security to all of your machines regardless of their location or join status?
With PolicyPak Admin Template Manager, you can deploy real group policy settings to any Windows desktop that has internet connectivity. Domain membership is no longer mandatory. Now you can enforce Windows updates and manage Microsoft Office macro settings for all of your machines in equal fashion. In fact, PolicyPak allows you even more control over admin template settings by incorporating item-level targeting, a feature that is only available natively to Group Policy Preferences. The screenshot below in Figure 6 shows the admin template policy creation process for Word and Excel security configuration settings.
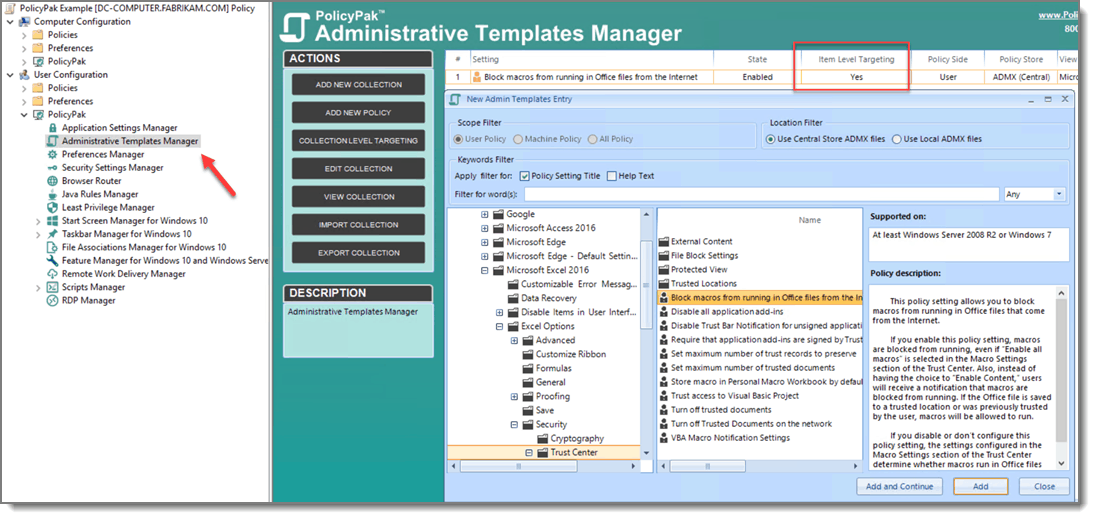
Figure 6: Creating an admin template policy with PolicyPak Admin Templates Manager.
You can watch of video demonstration on our website showing how to deliver Admin Template settings to non-domain joined machines over the internet.
ACSC Essential Eight: Manage and Control Third Party Applications
The two remaining mitigation strategies are “Patch applications” and “User application hardening.” ACSC application patching recommendations are identical to those for operating systems. User application hardening involves the blocking or disabling of Flash content and Java within web browsers. Both of these mitigation strategies are covered by PolicyPak.
PolicyPak Remote Work Deliver Manager can ensure that all of your Windows 10 applications automatically update hassle-free. Remote Work Delivery Manager uses your on-prem or cloud servers to copy applications and files down to any Windows machine whether it is domain-joined or not. Let’s say you wanted to install 7-Zip for your home-based remote users. Remote Work Delivery Manager supports multiple web-based storage locations including Amazon S3, Azure Blob Storage, and DropBox. In the example in Figure 7, we input the URL that points to the 7-Zip installer that we want to install.
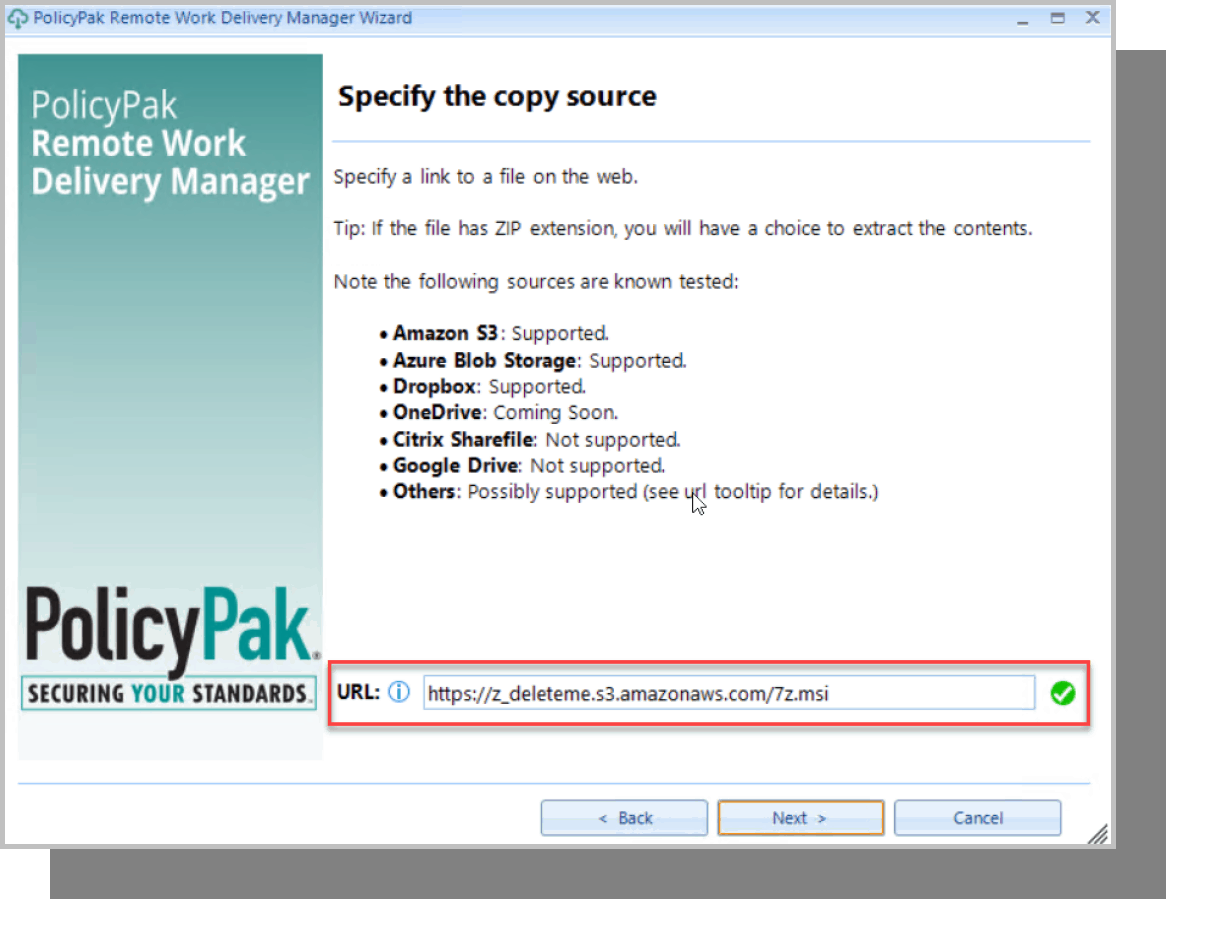
Figure 7: Installing 7-Zip to remote users.
You can choose to deploy a file or application just one time, or, as in this case, to always run it so that it always checks for a new version to deploy (see Figure 8). This means that the policy will kick in anytime you change the source file.
Figure 8: Choosing to copy files on every policy processing.
Up to this point, the policy is downloading the file from the web share. Now we add a process to the policy to install the latest app version as shown below in Figure 9. We can also add a reversion process to uninstall the app once the policy no longer applies.
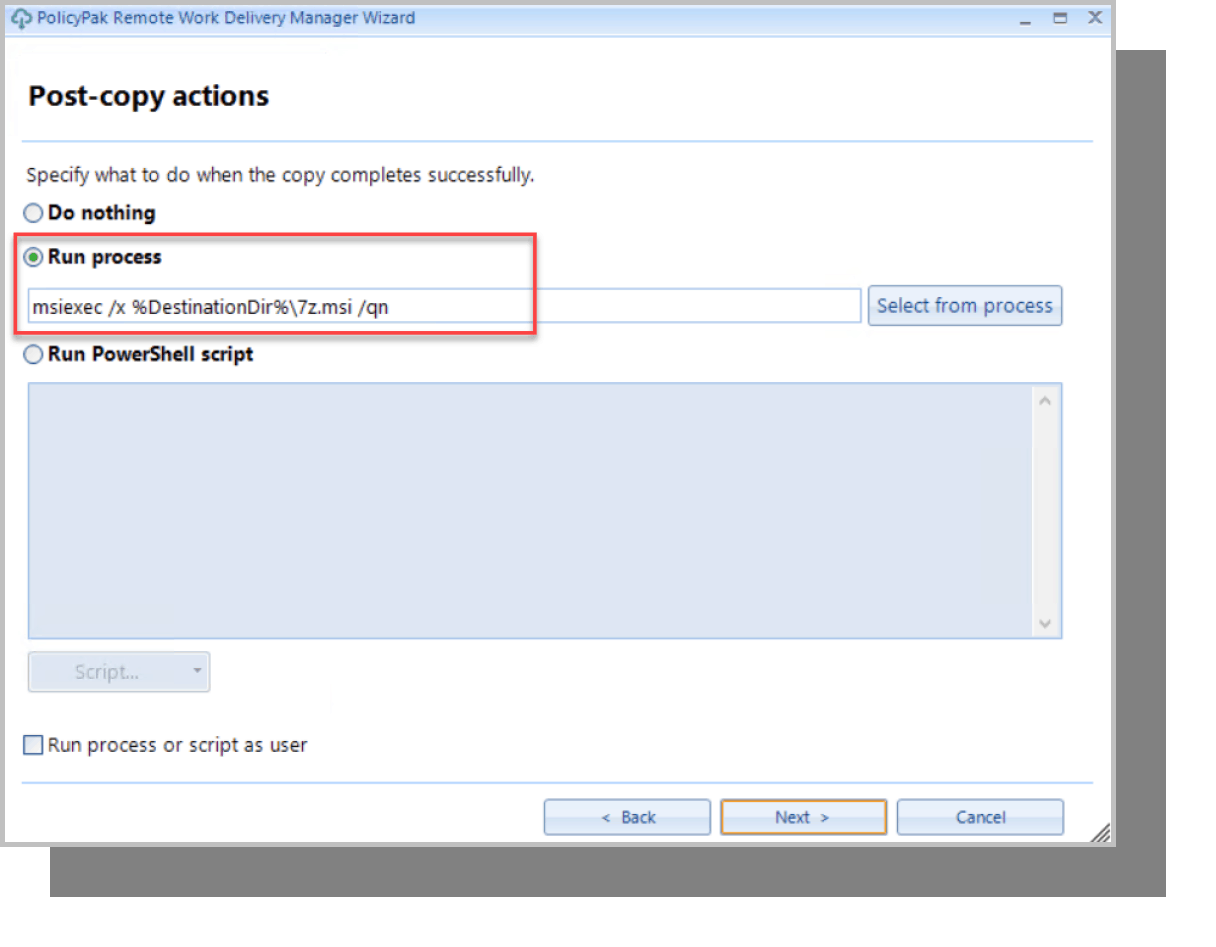
Figure 9: Selecting what to do after the file is copied.
After doing this, you will no longer have to install software to remote machines over the VPN connection. You can then deploy the policy using Group Policy, your favorite MDM solution, or PolicyPak Cloud to ensure that every computer is always running the most up-to-date version. You’ll never again have to assign a new update.
After being assured that users are always running the latest app version, it’s time now to configure and lock down the settings to that application with PolicyPak Applications Manager. PolicyPak Applications Manager gives you complete admin powers over the settings of hundreds of commonly-used applications including Firefox, Java, Flash, Chrome, IE, and Adobe products. You can also use PolicyPak Java Rules Manager to gain full control of your multi-Java environment. You can map websites to their optimal Java version or block Java websites altogether.
You can watch a video demonstration showing how to manage Firefox settings or just about anything else, including Chrome and Java on our website.
Summary
The Essential Eight is but one of a growing number of security guidelines and regulatory requirements being publicized and enacted today. While they come from different sources, they all involve similar procedures because cybersecurity is universal. Solution sets to combat today’s global cybersecurity threats can be found in one place, PolicyPak. Find out how PolicyPak can help you establish the highest maturity levels for the Essential Eight, or any other established set of cybersecurity guidelines present today.


