Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.
Block Adrozek Browser Malware Securely
Last month, Microsoft issued a security warning concerning a drive-by attack that targets Chrome, Edge, and Firefox users. It’s called Adrozek. While it is technically referred to as a browser hijacker or browser modifier, in reality, it is drive-by malware. Adrozek was first discovered back in May of 2020 and by August was infecting more than 30,000 devices on a daily basis. It is both sophisticated and malicious and needs to be on your radar.
Stop Cryptocurrency-Mining Malware Before It Starts (with PolicyPak)
In this white paper from PolicyPak, we will discuss cryptomining and cryptojacking, the insecurities they can create, and most importantly, how to secure your business from those insecurities, including: Enlist endpoint protection to secure against malicious code creation Remove / restrict local admin rights for standard users Increase browser security
What Adrozek Does
The core mission of Adrozek is to take control of your browser activities. Once that is achieved, the malware can alter your browser settings, allowing it to inject unauthorized ads into what appear to be legitimate search results. This is done through the use of malicious scripts that are downloaded from controlled servers. The unsanctioned ads often appear beside actual legitimate ads, making it difficult to discern what is actually real. Courtesy of Microsoft, you can see some side-by-side examples in the image below.

The attackers then earn money for any traffic generated by these ads through affiliated advertising programs. In essence, once your device is infected by Adrozek, your search results can no longer be trusted. While fake search results may not seem too threatening, there are other nasty repercussions of the malware as well.
- Microsoft reports that Adrozek can be used to monitor and steal passwords for financial and other sensitive websites. For those systems that have Firefox installed, Adrozek can confiscate encrypted user credentials from a victim’s Firefox profile that can be later decrypted and used by the perpetrators.
- Not only does Adrozek manipulate the browser, it increases the vulnerability of the infected browser’s attack surface. It does this by turning off security controls, disabling automatic updates, and turning off safe browsing, all of which exposes the hosted device to other types of attacks and malware strains.
- Once the attackers control a device through Adrozek, they can deploy future payloads of malicious intention. They can also sell access to their controlled devices to other cybercrime organizations at a nice profit.
24 Ransomware Tips That'll Save Your Bacon
reventing ransomware is a top cybersecurity priority, but mitigating the risk is easier said than done. According to an article by Cybercrime Magazine in 2018, it was predicted that a new business would fall victim to ransomware every 14 seconds in 2019, and by 2021, that time would decrease to just 11 seconds. To help you protect your Windows 10 desktop environment from ransomware, we’ve compiled a list of 24 crucial steps you should take into account today! You should use these steps in conjunction with one another as part of a multilayered strategy; do not depend on any one of them individually.
How to Diagnose Adrozek
So how do you know if you have Adrozek on your computer? The most obvious indication is an abrupt increase of pop-up and banner ads within your web sessions. You might see a sudden deluge of video commercials. At the least, you may realize that your search results don’t seem quite right or your browser is taking you to websites you aren’t asking for. Another indicator may be slower than normal computer performance. A tell-tale sign is the presence of a new .exe file located in the %temp% folder under Program Files. Adrozek itself poses as a legitimate Windows service once the infected .exe file becomes rooted.
How to Eliminate Adrozek once Infected
If you suspect that Adrozek has infected your machine, you need to act as soon as possible due to its ability to steal credentials. You have several options to get rid of this dangerous menace.
- You can manually remove suspicious add-ons and extensionsfrom your browser. Chrome users can use the Chrome Cleanup Tool as well.
- You can use System Restore to return the machine to an earlier point prior to the infection incident.
- You can use a variety of adware, spyware, and antivirus tools to remove the infection.
- You can follow Microsoft’s recommendation to re-install your infected browsers.
How to Combat an Adrozek Infection without PolicyPak
Like all drive-by malware, there aren’t many sure ways to prevent an Adrozek attack on your enterprise devices. A modern-day endpoint solution that is regularly updated goes a long way in preventing an infection. You can remind your users to stick to well-known websites and refrain from clicking banner ads or unknown hyperlinks (good luck on that one). If these solutions dependably worked for the most part of course, we wouldn’t have an overwhelming malware infection rate.
The fact is that there is only one sure method to lock down the attack surface of your Windows 10 computers and that is through Allow Listing. The problem with allow lists of course is that they require a lot of maintenance as these lists must be perpetually updated. For that reason, many enterprises admins fail to implement them.
How to Combat Adrozek with PolicyPakAdrozek and other strains of drive-by malware silently sneak into a user’s device unabated through a piece of software that seems insignificant and harmless. That is where the battle must be won. By preventing users from interacting with unauthorized files in the first place, drive-by malware attacks can be kept at bay. You just need an easy way to do that. That is what PolicyPak Least Privilege Manager does.
Kill Local Admin Rights
Manage local admin rights and elevate only the permissions users need. With two versions to choose from, the PolicyPak Least Privilege Security Pak can meet any organization's security and compliance requirements for least privilege management.
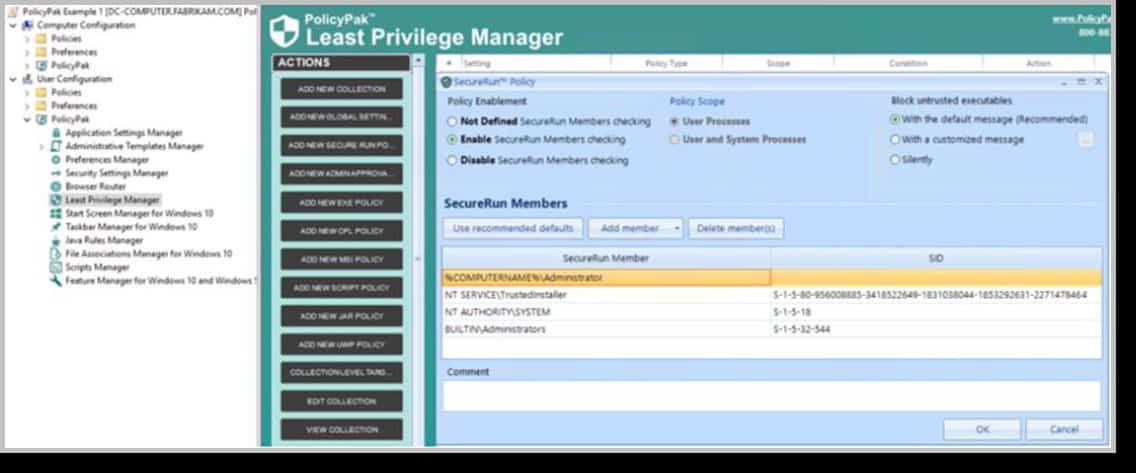
To begin with, PolicyPak Least Privilege Manager uses our signature security tool, SecureRun™, to provide blanket level protection. Think of it as a blanket Allow List without the hassle. Its untrusting nature makes it ideal for any zero-trust strategy. It doesn’t trust the user, nor the files that the user is clicking on. It operates under the simple premise that when users download files off the Internet or copy them from a USB drive, they own the file and must be on a list of trusted user to be able to run it, as seen in the following screenshot.

When SecureRun™ is on, PolicyPak Least Privilege Manager checks to see who owns the executable, MSI, script, or Java JAR file. SecureRun™ then maintains a list of who can initiate new processes. Below is an example of the default list, which you can modify to your needs.
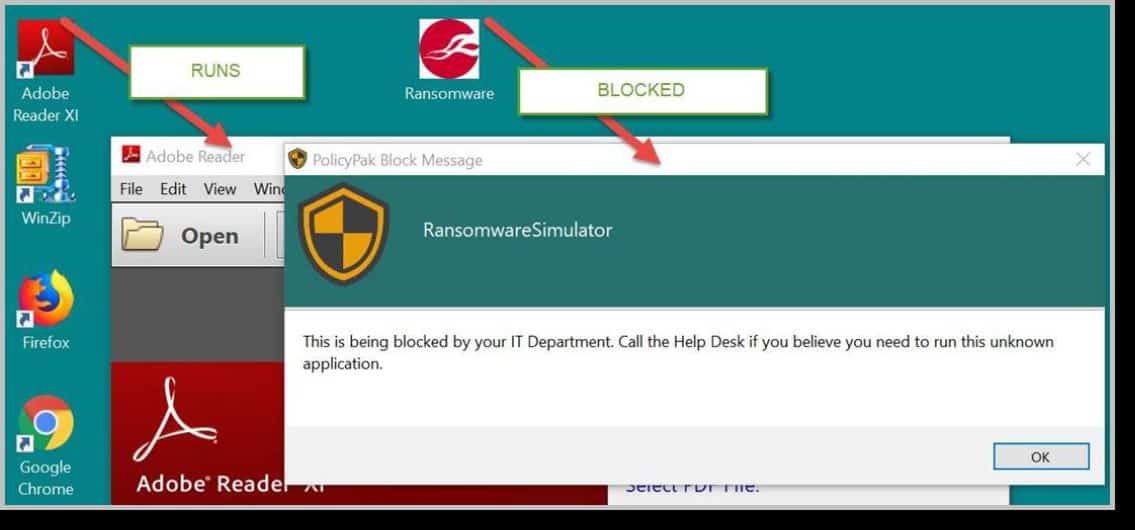
A user that is not on the SecureRun™ Members list is not trusted, thus processes originating from that user are blocked. The result is that properly installed applications can run perfectly well, but all unknown applications and scripts are blocked, as shown below in the following screenshot.
You can watch a video demonstration on our website on how to ensure that Adrozek, ransomware, and even zero-day attacks are kept at bay.
Adrozek is but one of thousands, even millions, of drive-by malware attacks that will threaten your enterprise devices over the coming year. With the blanket protection of PolicyPak Least Privilege Manager, however, it only takes a few clicks of the mouse to combat all of them. Keep your search engine results legitimate and your credentials secure with SecureRun™.





