Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.
Don’t Disable Device Guard Just Yet, Here’s Why
Microsoft has placed a lot of emphasis on security with Windows 10. They have introduced so many tools, including Device Guard, Credential Guard, and Windows Security Center, that it can get a bit confusing determining the role for each one.
The fact that Microsoft also changes the names of some and deprecates others adds to the uncertainty as well. We are not here to diffuse all the possible confusion.
In this blog, we focus on Device Guard. Device Guard is available in Windows Enterprise and Education editions of Windows 10 as well as Server 2016 and 2019. Let’s outline what Device Guard does, how you enable it, who should use it, and what alternatives are available.
Virtualization Based Security
Both Device Guard and Credential Guard depend on something called Virtual Secure Mode (VSM). You might not think about virtualization as a security tool, but virtualization is all about segmentation.
Think about it.
A virtual machine gets separated from the hardware of its residing host, and its internal processes are isolated from those of other virtual machines (VMs). VSM is based on the same concept and leverages the traditional hypervisor to secure the desktop.
In VSM, specific processes and their associated memory become isolated from the host operating system.
Think of it as a bubble sitting on top of the hypervisor where malicious code can operate independently of the host OS and the hardware underneath.
#1 Applocker Alternative
In the box is Microsoft AppLocker, and it has a lot to offer; if you care to keep it maintained with a lot of care and feeding. But even then, AppLocker doesn’t address the number one concern of admins which is how to remove local admin rights. And, AppLocker doesn’t work at all with Windows Professional machines; only Windows Ultimate.
How to Enable Device Guard in Windows 10
To enable Device Guard, we first need to enable the Hyper-V hypervisor on our Windows 10 machine. (Of course, keep in mind that your hardware must support virtualization to enable the hypervisor. You may have to make changes to your BIOS before this step.)
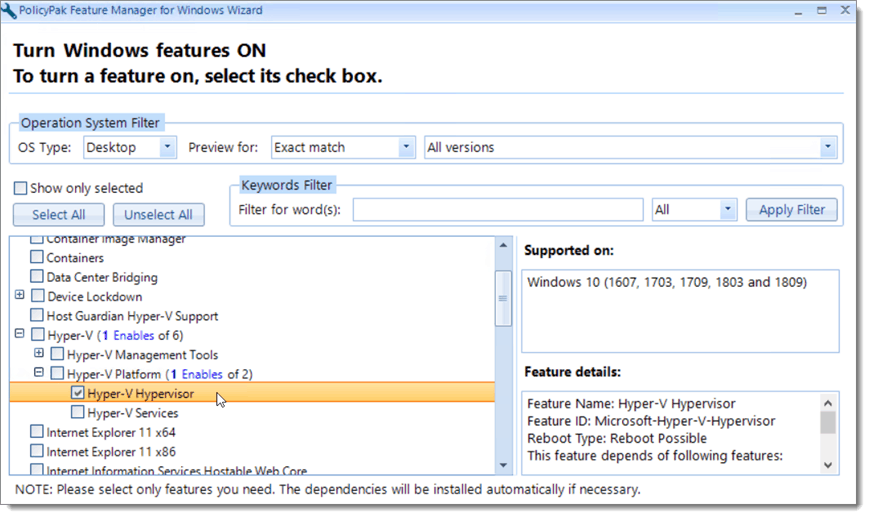
The hypervisor is enabled using the Programs and Features applet in Control Panel. This operation can be cumbersome to do for an entire fleet of Windows devices. It doesn’t have to be, however. By using PolicyPak Features Manager for Windows, you can add or remove Windows 10 classic and optional features at will. Because PolicyPak integrates with Group Policy, all you have to do is create a GPO and create a policy, as is shown below.

Note that before version 1609, you had to enable a feature called “Isolated User Mode.” That is no longer necessary. Simply choose the Hypervisor feature, and that’s it! In the screenshot below, we have selected the Hyper-V Hypervisor feature using PolicyPak, and on all the target machines, it gets instantly applied.
You can see a video demonstration of PolicyPak Features Manage for Windows here.
How to Configure Device Guard
Now that we have hypervisor enabled, we can move on to Device Guard. Device Guard is a group of key features designed to harden computer systems against malware. It is is a part of what Microsoft calls Virtualization Based Security. Since Windows 10 v1709, Device Guard gets split into two separate features – Windows Defender Application Control and virtualization-based protection of code integrity.
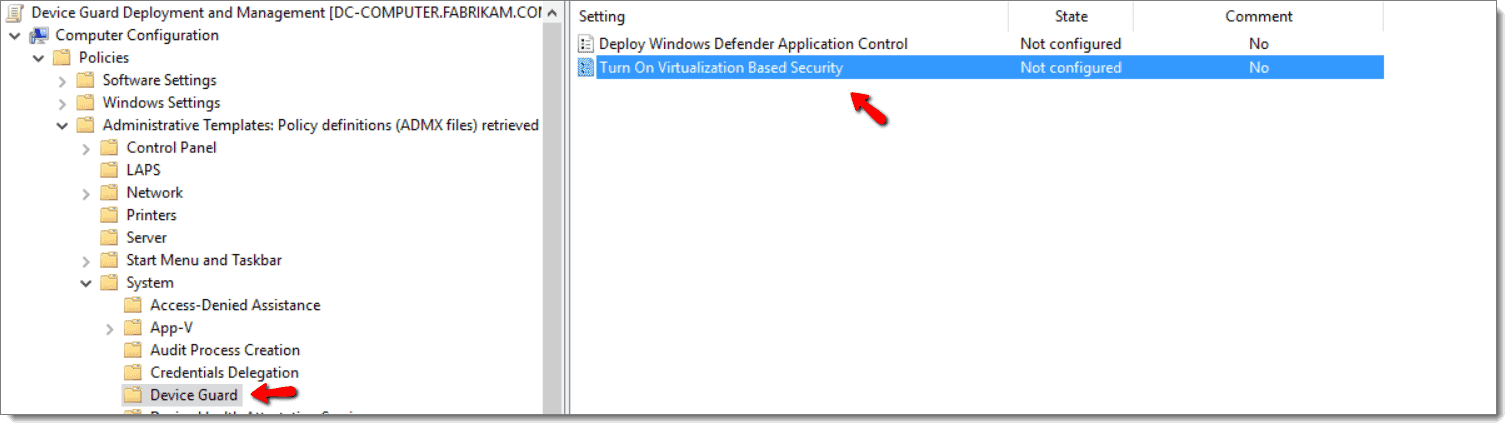
You can use Group Policy to deploy your Device Guard settings by creating a GPO and go to Computer Configuration > Administrative Templates > System > Device Guard.
How to Deploy Device Guard with PolicyPak
You can also use PolicyPak Administrative Templates Manager to deploy Device Guard or any ADMX setting. There are several advantages to using PolicyPak Administrative Templates Manager over Group Policy, such as the ability to utilize Item-level Targeting. You can also export and import settings for devices that may not be on-premise or managed by MDM. PolicyPak updates the ADMX templates as soon as Microsoft releases them, so you have access to all settings. In the screenshot below, I have enabled Secure Boot with DMA protection. I have also enabled the “EUFI lock option to prevent the code integrity option from being disabled remotely.

You can see a full demonstration of PolicyPak Administrative Templates Manager here.
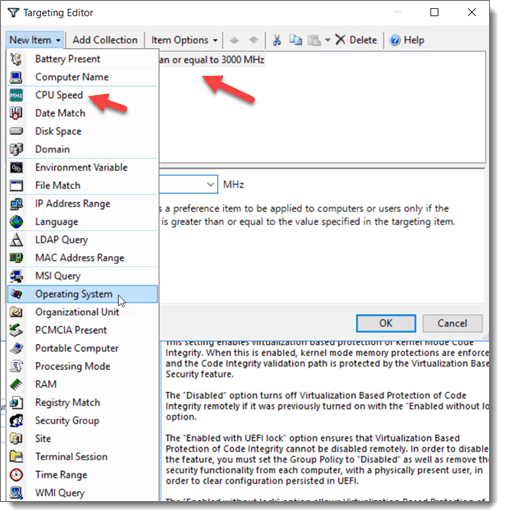
Anyone who has worked with Group Policy Templates knows the granularity capability it brings to deploying policies. PolicyPak Templates Manager gives you the exact targeting power for Administrative Template policies as well. Because VBS uses extra processing power, I am going to require a minimum processing speed for targeted devices. I am also going to choose Operating System as one of the targeting items and specify the OS and version number I want.
Now let’s enable Application Control. Long story short, you must first create a code integrity policy from a “golden computer.” Then you use PowerShell to create the policy and convert it to a binary file and point the Code Integrity Policy file path setting to it within the Windows Defender Application Control feature.

Application Control is a hardcore whitelisting application that ensures that only trusted applications run. While AppLocker performs whitelisting as well, Application Control is more robust as it is VSM protected and thus supported by a chain of trust from the hardware through to the kernel. The problem with Whitelisting, however, is applications come and go.
Every time a new application gets introduced into the organization, the golden computer must be modified, and the required processes repeated to generate a new application list. This process requires a significant amount of effort and time occupied with mundane tasks. For this reason, you probably only want the full suite of Device Guard features on computers with critical applications and services such as shop floor computers, ATM and cash register systems in which the desktop environment rarely changes.
Another instance might be student laptops for a K12 one-to-one program. Of course, as mentioned, Device Guard is only available in Enterprise and Education edition, so if you use Pro Edition, it’s not an option.
Device Guard Alternative
Whitelisting sounds like a wonderful way to ensure that only trusted applications can run, but it is short on practicality. There is a better way, in any case. PolicyPak least Privilege Manager prevents standard users from running non-sanctioned applications, thus preventing malware and “unknownware” from running. The methodology is simple. PolicyPak Least Privilege Manager strips standard users of local admin rights. Items that require Admin rights then run with elevated privileges. Once admin rights get stripped, PolicyPak Least Privilege Manager can be configured to simply block all items that are not “properly installed” by the admin; this is called PolicyPak SecureRun™ policy, as is shown below.

When SecureRunTM is on, PolicyPak Least Privilege Manager checks to see who owns the file executable, MSI, script, or Java JAR file. When users download files off the Internet or copy from USB drive, etc., they own the file, as is shown here.
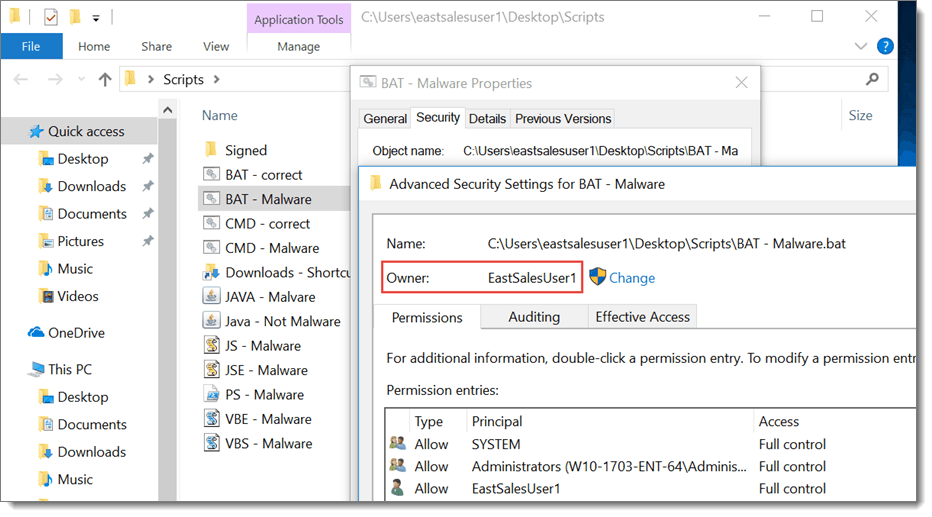
But SecureRun™ defines a list of users allowed to install the software. See the default list in the screenshot below.

And any application not installed by a member of the list is forbidden. In this example, SCCM installed Adobe Acrobat, and therefore the SYSTEM owns it. But, the user downloaded Malware.BAT, and as a result, was automatically blocked.

No more “golden computers.” No more forever updating the list of trusted applications. Just a single policy that you set and forget. What’s more, PolicyPak Least Privilege Manager supports many more operating systems and editions as well.
- Pro, Enterprise and Ultimate editions of Windows 7
- Pro and Enterprise edition of Windows 8
- Any edition of Windows 10 (Pro, Enterprise, Education)
- Server 2008 R2 and later
You can see a full video demonstration of PolicyPak SecureRunTM here.
Next Steps
Windows has significantly improved desktop security. While the premise of Virtualization Based Security is effective in isolating malicious code from the OS, the application control features of Device Guard are painful and ungainly to deploy and maintain over time. Microsoft has many security tools available. Some are better than others.
At PolicyPak, we strive to supercharge policy management, secure the desktop, and make the job of the administrator easier. That is the premise behind the entire PolicyPak suite of solution components.



