Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.

Intune Compliance Policies: Get Started in A Few Easy Steps
The title of article in Forbes Magazine said it best, “Awash In Regulations, Companies Struggle With Compliance.” Whether it’s HIPAA, PCI-DSS, GDPR, CDPA, or the recent Virginia CDPA, compliancy regulations are piling up and business leaders are making compliancy a priority. Compliancy can be a real challenge, however, when it comes to mobile computers. Out of sight can equate to out of mind, allowing non-compliant laptops to slip through the cracks. That’s why it’s so important to have a system to enforce basic compliance standards. Using an MDM solution, such as Microsoft Endpoint Manager (Intune), can offer a simple way to enforce a basic level of security. For Intune, this involves two main steps.
- Define the rules and settings that users and devices must meet in order to be compliant.
- State the applicable actions for devices that are noncompliant.
Intune Compliance Policy Settings
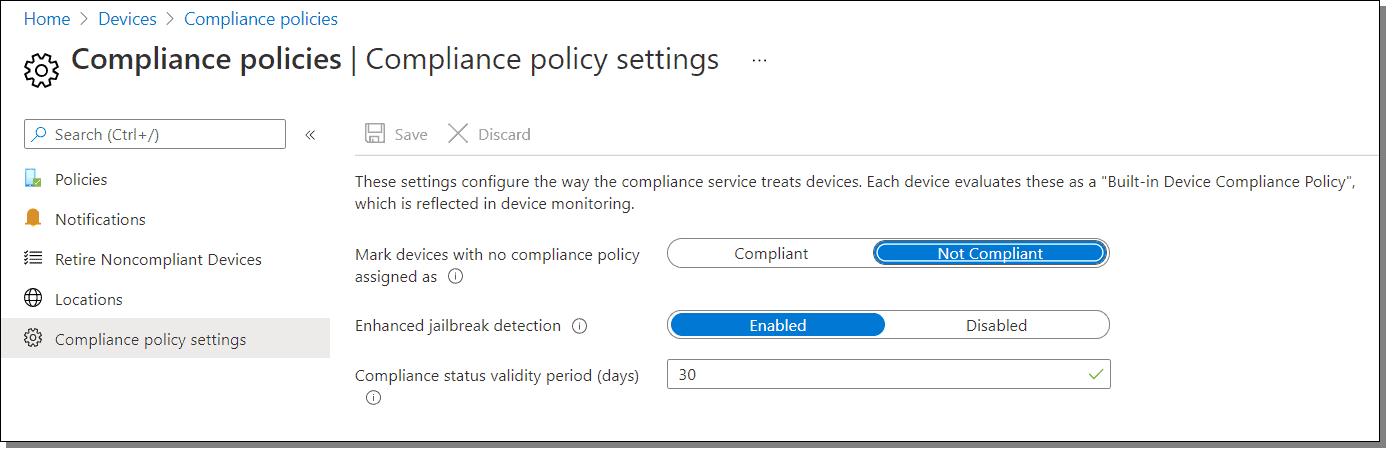
Intune compliance policy settings are deployed tenant-wide, regardless of the device compliance policy settings you choose to enforce or the settings you might configure in the device compliance policies. To create a compliance policy you can either go to Endpoint Security > Compliance Policy or go to Devices > Compliance policies. There are only a few settings to configure, as shown in the image below. The most notable option is the enabling/disabling of the “Not Compliant” label for devices with no compliance policy. Note that there is also a feature for enhanced jailbreak detection, which only applies to iOS devices. Jailbreaking allows root access to iOS devices which isn’t a good thing from a compliance point of view.
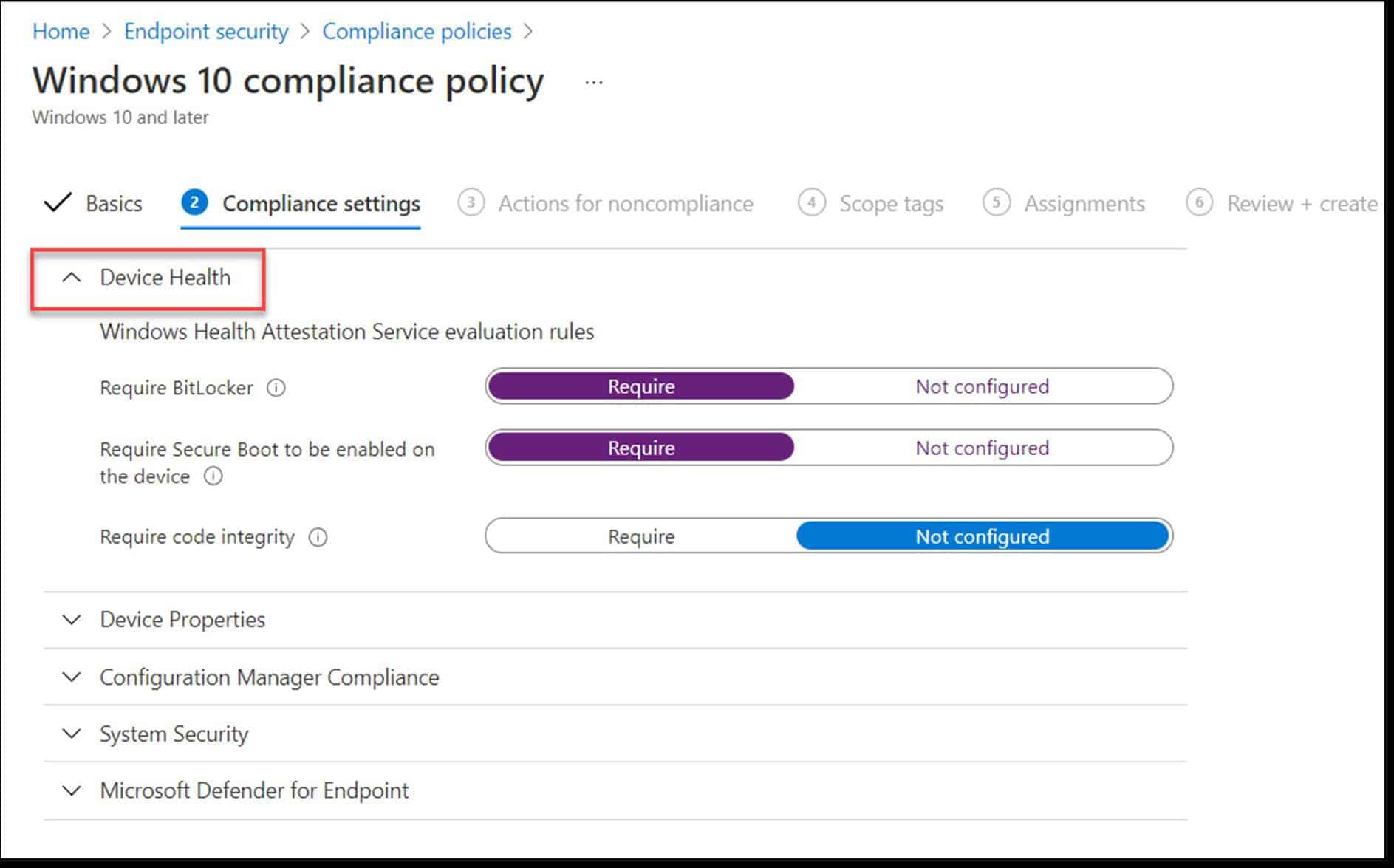
Once you have your tenant-wide compliance policy settings enabled, you can create device compliancy policies by navigating to Endpoint Security > Device compliance. After naming your new policy, you can start configuring the settings you want to enable. Two classic examples include enforcing BitLocker activation and requiring Secure Boot to be enabled, as shown in the image below. Other settings include minimum password requirements or minimum OS version.
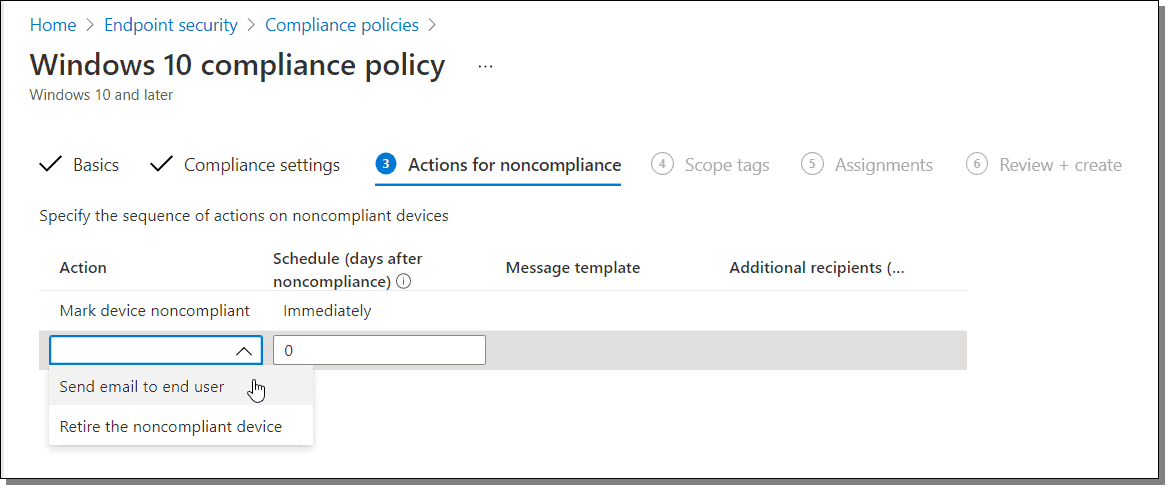
The next step is to designate the desired action for non-compliancy. In most cases this means notifying the user, but one can choose to retire the device as well (see image below). Retiring refers to the process of removing all company data off the device and removing it from Intune management. Once retired, the device works on its own independently.

The final step in the policy creation process is to assign the policy to a group. You then need to configure settings for the non-compliance actions you chose. For email alerts, go to Compliance Policies > Notifications and configure your desired settings as shown below.
Note that devices are not automatically retired if you choose the retire action. Instead they are added to a list in the admin console that resides at Devices > Compliance policies > Retire Noncompliant Devices. An admin must then manually retire the device from the list by selecting one of the menu options as shown in the screenshot below.
You can bolster the power of your compliance policies by teaming them with conditional access policies. Conditional access policies allow you to assess the results of your configured device compliance policies in order to determine which devices can access your organization resources. A conditional access policy works like an if–then statement. If your device is compliant, then it is granted access. Non-compliant devices are not granted access.
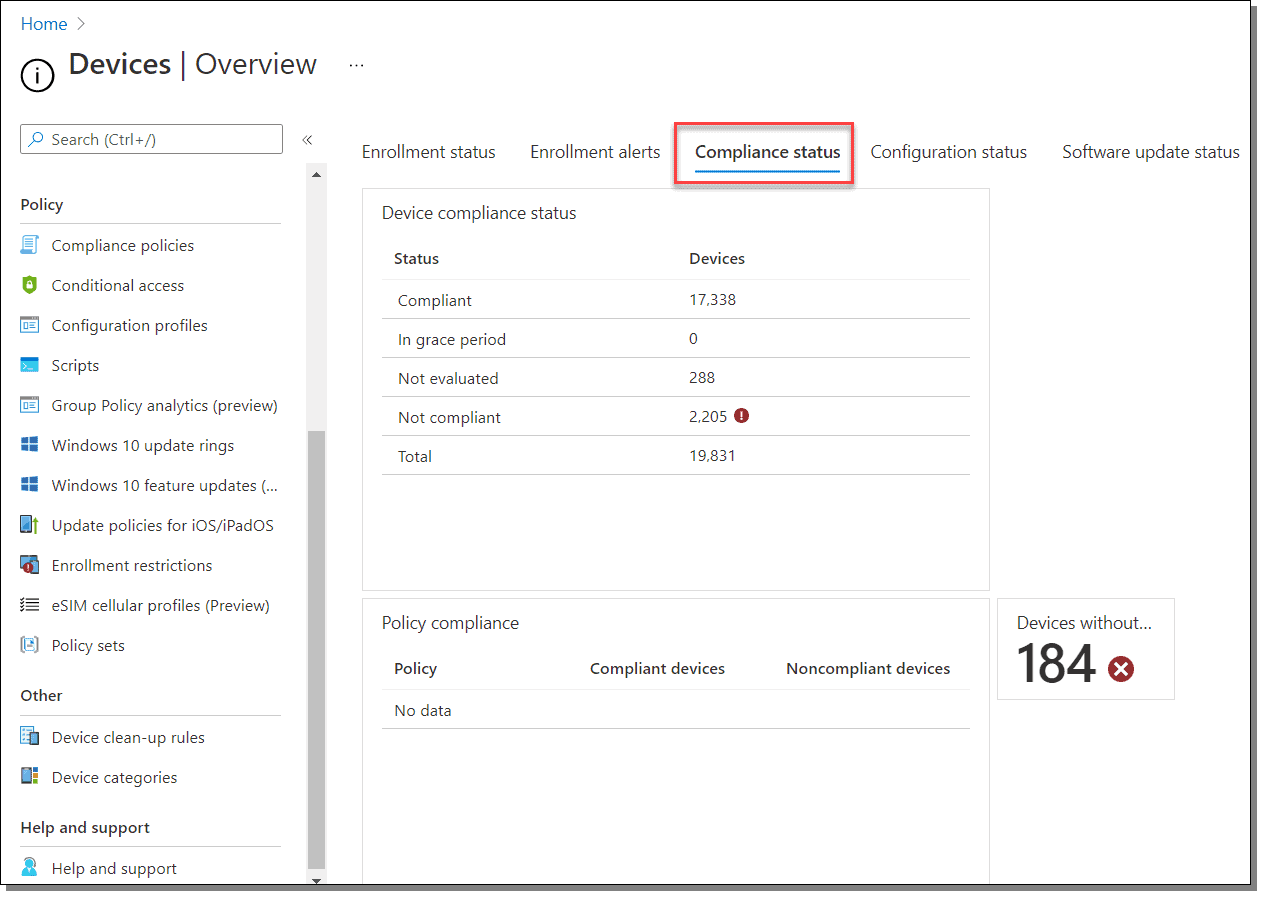
You can also monitor device compliance and troubleshoot compliance-related issues in Intune by going to Devices > Overview > Compliance status. This allows you to determine the following:
- Overall compliance status of your devices
- Compliance status for an individual setting
- Compliance status for an individual policy
- Specific settings and policies within individual devices
The screenshot below shows an example of the information provided on the “Compliance status” screen.
Other Types of Compliance Policies
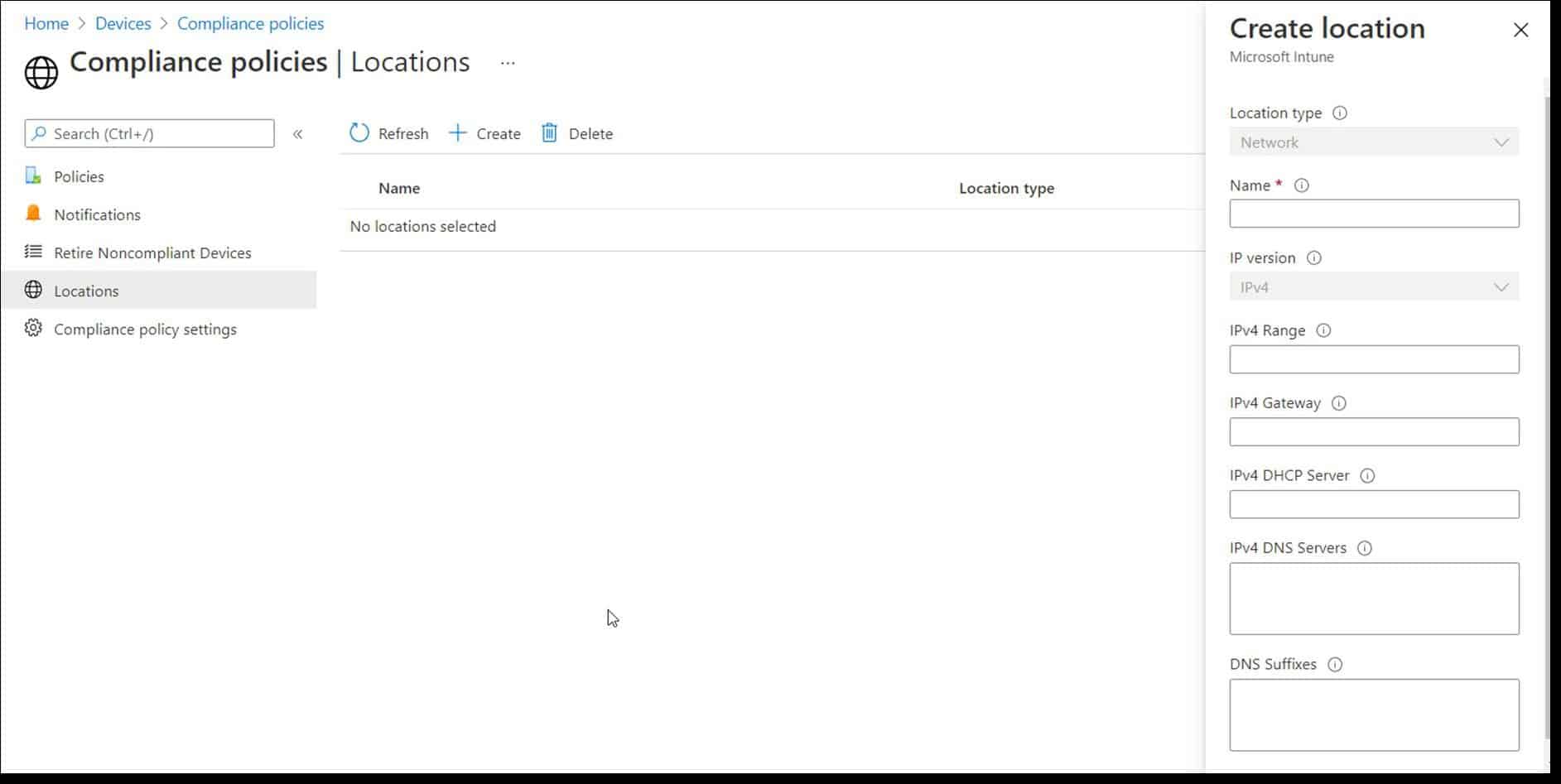
In some cases you may want to block devices from accessing the corporate network once they leave a designated location. You can do this by creating network location-based compliance policies, also referred to as network fencing. To do this, create a compliance policy that uses locations identified by their IP address. The policy will define the action taken when the device is no longer connected to that network location. You can then team this with a conditional access policy. The screenshot below shows the options available in a network location-based compliance policy.
Compliance Is Not Security
Ensuring compliancy does several things for you.
- Satisfies compliance regulations
- Helps you to avoids fines for non-compliancy
- Makes your enterprise safer
Note that we used the word, “safer” here. The dirty little secret is that you can be in perfect compliance with a cybersecurity standard or regulation and still have an incident or a hack. Despite having absolute compliance, you can still be far short of absolute security. The fact is, you need more than just Intune compliance policies to secure your mobile machines.
PolicyPak Least Privilege Pak for Security
PolicyPak is a modern desktop management system that simplifies management, security, automation, and reporting for all of your Windows computers whether they are domain-joined, MDM-enrolled, or standalone devices. With PolicyPak Least Privilege Security Pak, you can enforce least privilege security standards by delegating only the permissions that standard users require. You can then use PolicyPak Least Privilege Manager to create policies that elevate only the applications and system tools your users need. Doing so bypasses the interruption of UAC prompts that impede the natural work flow and initiate a helpdesk session. The discontinuance of broad local admin rights helps ensure your devices remain compliant as well. Because all policies created with PolicyPak can be imported into Intune or any of the major MDM solutions, PolicyPak Least Privilege Security Pak is a perfect complement to MDM compliance policies.
For more information, you can watch this video demonstration on how to enable online and offline users to overcome UAC prompts via Admin Approval.
Now, let’s combine least privilege compliance with PolicyPak’s signature security tool, SecureRunTM . Think of SecureRunTM as a blanket Allow List without the hassle. Its untrusting nature makes it ideal for any zero trust strategy. It doesn’t trust the user, nor the files that the user clicks on. It operates under the simple premise that when users download files off the Internet or copy them from a USB drive, they own the file and must be on a list of trusted user to be able to run it, as shown in the following screenshot.
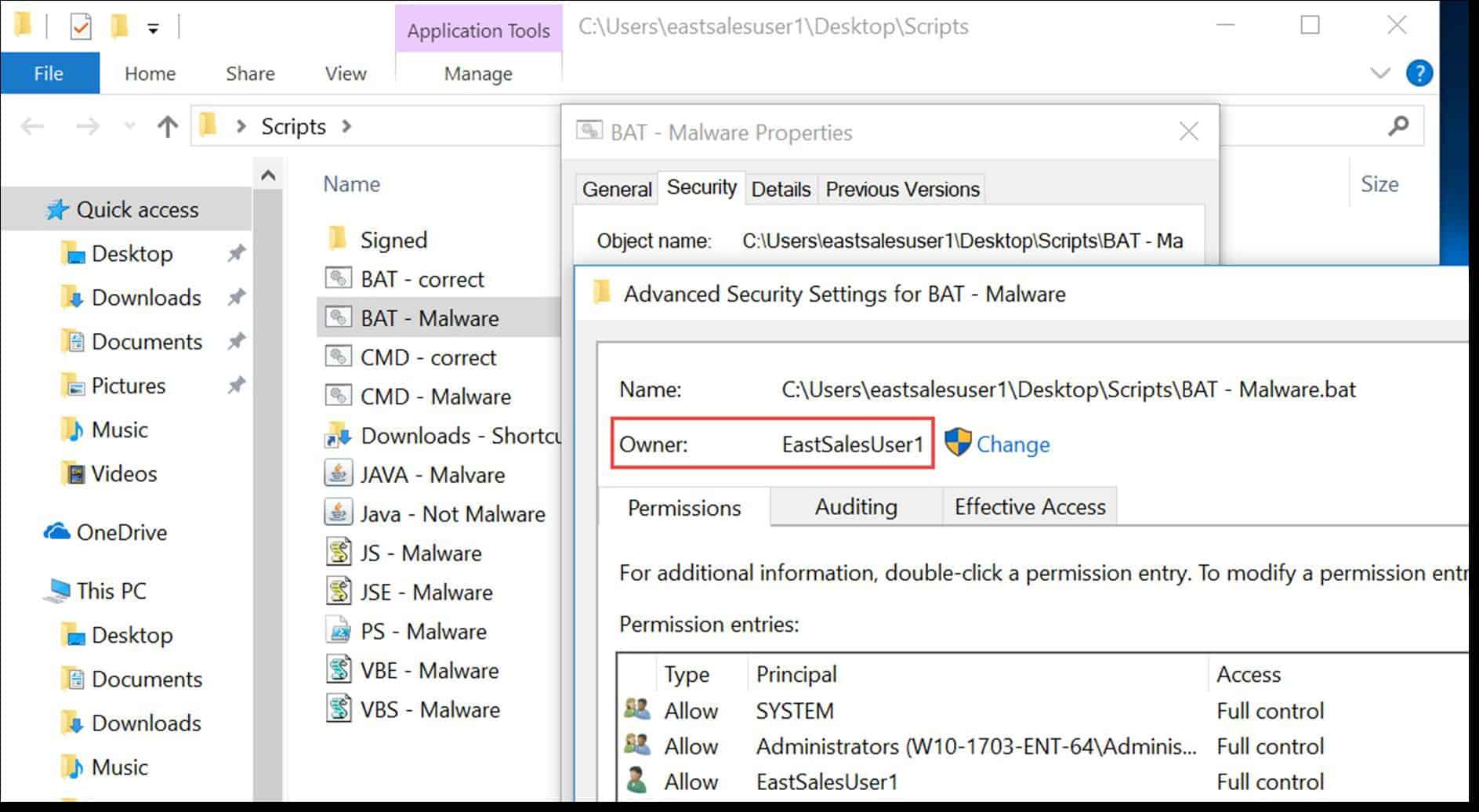
When SecureRun™ is on, PolicyPak Least Privilege Manager checks to see who owns the executable, MSI, script, or Java JAR file. SecureRun™ then maintains a list of who can initiate new processes. Below is an example of the default list, which you can modify to meet your needs.

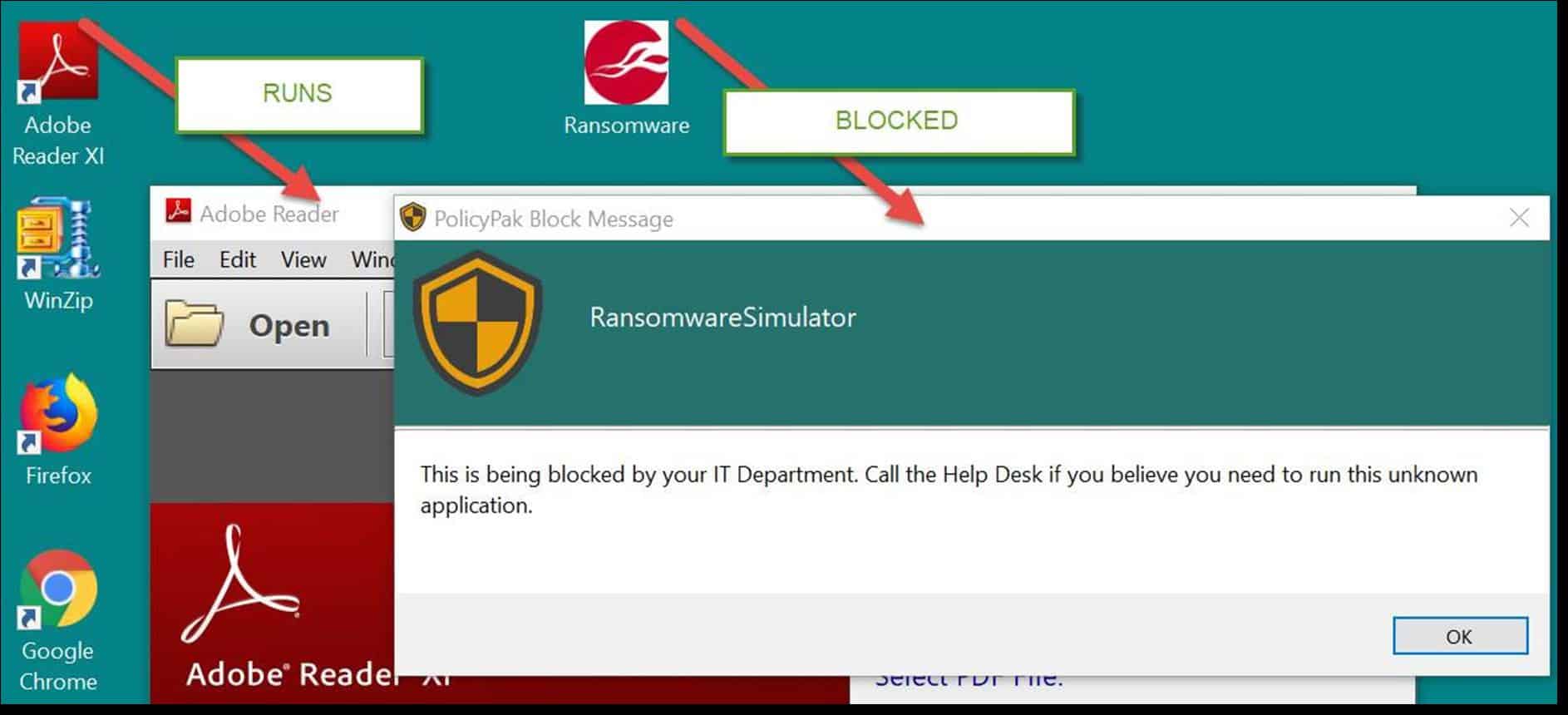
A user that is not on the SecureRun™ Members list is not trusted, and SecureRun™ blocks processes originating from that user. The result is that properly installed applications can run perfectly well, but all unknown applications and scripts are blocked, as shown below in the following screenshot.
Summary
Microsoft Endpoint Manager is a great way to help ensure compliancy for your mobile devices. But compliance alone isn’t enough when it comes to preventing malware and ransomware attacks. Strengthen your compliancy efforts with the total package of PolicyPak.


