Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.

Domain-Joined vs Non-Domain-Joined: Best Management Tool
The case to domain-join or non-domain join is the decision network administrators and domain administrators must make for work and school networks.
For many years, domain-joined was “the way” that enterprises chose to secure and manage their Windows domains. It was a tried and true method; it was the only way to ensure that you could manage Active Directory users and computers centrally. Central management is essential when it comes to protecting your computer network because your enterprise is only as secure its weakest link. It only takes one user account with a weak password or local admin rights to invite hackers and advanced malware into your enterprise environment and operate unabated. Central management also provides huge efficiencies for IT admins to manage all applicable enterprise devices.
The Domain Join Model
Let’s take a look at how the traditional approach of domain joining computers has benefitted IT admins over the years.
- It provides central authentication so that users can authenticate one time to the network and then access the resources they need, assuming they have permission to them.
- Enforces a uniform password policy across the entire domain to ensure that all users utilize passwords that meet the minimum organizational requirements.
- Implements security policies can be implemented to lock down devices such as enforcing lock screen settings
- Enables Domain Admins to assign resources to domain users such as printers, applications, services, and network shares across the domain
- Invokes the ability to use the combined powers of Group Policy and Group Policy Preferences. Over 10,000 configuration settings to both users and computers across the domain, giving IT granular control across the entire domain.
Of course, the list above only skims the surface. For many reasons, domain-joining computers have proven to be a highly effective approach to securing and managing large numbers of devices. It was superior to non-domain joined without question. However, that was in day in which management functionality between domain-joined and non-domain was a gaping divide. Other than the smallest of networks, there was no question concerning which path to undertake.
Non-Domain Join is no longer Isolating

While domain join is still a great option, it is not the only option. There are many important reasons for this.
We live in a mobile world in which computing devices leave the secure confines of the network regularly. Some advantages to being non-domain joined include:
Migrating services, applications, and resources to the cloud to digitally transform themselves and attain greater scalability and agility.
Embracing Windows-as-a-Service rollouts.
Embracing the idea of Consumerization of IT, which has introduced dilemmas to internal IT such as BYOD and Shadow IT.
Using non-Windows machines (for a growing number of enterprises, it isn’t just a Windows world anymore.)
Limiting malware outbreaks to one or a few machines instead of a whole domain.
It used to be that a non-domain joined status meant isolation. A non-domain joined computer was restricted to the status of being in a lowly workgroup in which every machine was an island unto itself.
That is no longer the case thanks to cloud computing platforms such as Azure and Intune and other MDM service provers. Today, admins can manage thousands of non-domain joined machines through a single management portal.
MDM Enrollment can provide you domain-like management
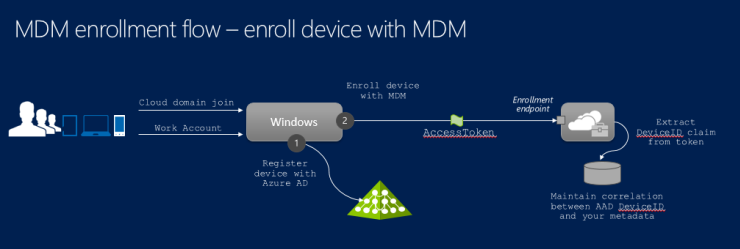
MDM enrollment has redefined what it means to manage non-domain joined machines.
MDM enrolled machines reside in a cloud tenant such as Azure. While its name implies that it only applies to mobile devices such as phones, tablets, and laptops, MDM can manage traditional desktops too as long as they are MDM enrolled.
While Intune and other MDM solutions fail to offer the exhaustive array of configurable settings that Group Policy does, it fills a significant void that exists today in the traditional domain world. As long as an MDM machine connects to the internet, admins can manage it no matter where it may be. MDM makes it a perfect choice for organizations that have large fleets of mobile devices or remote workers. Some of the critical features of Intune include the following:
- The ability to reset or wipe a machine
- Enforce passwords and other security policies and establish security baselines
- Provide admins the ability to track security events and actions initiated by users
- Allow or ban minimum or maximum operating system versions
- Deploy applications, PowerShell scripts, and wireless SSIDs
- Manage Windows 10, iOS and Android devices through a single portal
Intune also allows admins to manage designated Windows components such as Windows Security Center.
It can also disable designated component functionality such as Control Panel applets. Intune isn’t trying to overtake or perform all of Group Policy’s functions. But what it does well, it does well.
So which one is better? Domain Joined or non-domain Joined?
With the advancement of cloud management and computing solutions, the question to the original question of domain join or non-domain join is no longer straightforward. While it may seem that Microsoft is pushing everyone to the cloud, Microsoft continues to support both methodologies.
In no way, is Group Policy dead, as Microsoft publicly confirmed several years ago. This news is good for companies that must continue to support legacy systems and applications built for an on-prem domain environment. Companies with an established management system such as SCCM, PDQ Deploy, or KACE ]probably want to maximize their existing investments and continue to domain join their devices.
The same is true for those who continue to use existing imaging solutions to deploy and configure their devices. A brand new startup, on the other hand, may choose to implement a cloud-first approach and maximize the agile nature of the cloud for their entire enterprise.
Mixed and Hybrid Environments: Domain Joined, and MDM enrolled (DJ++)
Some enterprises may want to host a mixed environment of domain-joined and non-domain joined devices. An example might be an enterprise that issues laptops to contractors and traveling employees. Under this scenario, traveling devices can be managed through Intune, while on-premise desktops and servers reside within the traditional AD domain.
Some organizations may choose to implement hybrid Azure AD joined devices. In this way, admins can still manage and secure business-critical desktops and servers, while utilizing MDM to manage mobile devices, kiosk computers, shared PCs, and other generic machines.
How PolicyPak Supports Both Domain Joined and Non-Domain Join Machines

PolicyPak has the Group Policy edition, which is ideal for your domain-joined world.
PolicyPak also has the MDM edition, which is ideal for your non-domain joined computers.
With PolicyPak, IT admins can increase their management of domain-joined machines; and IT admins can increase their management of non-domain joined machines.
With PolicyPak, you work the way you want to work.
- Using PolicyPak Administrative Templates Manager, admins can configure and deploy ADMX/ADM template setting to MDM enrolled machines or unmanaged non-domain joined machines.
- Use PolicyPak Security Settings Manager to deploy real Group Policy Security settings with your own systems management software or deploy them over the internet through your MDM service
- Use PolicyPak Preferences Manager to deploy GPP configuration settings to non-domain joined machines and enforce them even when devices are not connected.
- Use PolicyPak Least Privilege Manager to remove local admin rights and enable standard users to do admin-like tasks.
PolicyPak has a host of other tools that provide solutions that admins are clamoring for today, such as default browser enforcement, managing third party application settings, and enforcing the security concept of least privilege to all of your standard users. All of our solutions come in on-prem and cloud-based editions.
At PolicyPak, we make it, so you don’t have to choose: computers which are domain joined or non-domain joined are both first-class citizens.


