Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.
NIST 800-171: How PolicyPak Helps You Meet Compliance
The NIST SP 800-171 mandate lists fourteen security controls that must be addressed in order to safeguard covered contractor information systems. Many companies are having to deal with an increasing number of data regulations, such as the General Data Protection Regulation (GDPR) and the California Consumer Protection Act (CCPA). These regulations were created to protect the personal and sensitive information of private citizens and affect organizations across a multitude of industries. Consider, in addition, the critical importance of securing data that is related to the security of the United States. This is the purpose of the Defense Federal Acquisition Regulation Supplement (DFARS) regulation, which went into effect December 31, 2017.
DFARS 252.204-7012 requires that all contractors wanting to do business with the Department of Defense (DoD) must adequately protect controlled unclassified information (CUI) within nonfederal information systems and organizations. CUI consists of sensitive information containing proprietary business interests as well as all sensitive information relevant to the interests of the United States. DFARS does not apply to contractors whose products and services to the DoD are commercially available off-the-shelf (COTS). DFARS compliance also extends to contractor suppliers as well.
NIST 800-171 Controls
Of course, the word “adequate” is quite vague, which is often characteristic of industry security related compliances. In order to provide better guidance and ensure conformity across the industry, NIST Special Publication 800-171 was added as a requirement. The list of fourteen NIST SP 800-171 security controls are as follows:
- Access Control
- Audit and Accountability
- Awareness and Training
- Configuration Management
- Identification and Authentication
- Incident Response
- Maintenance
- Media Protection
- Physical Protection
- Personnel Security
- Risk Assessment
- Security Assessment
- System and Communications Protection
- System and Information Integrity
There is no single solution to ensure compliance concerning DFARS, HIPAA, CCPA, or any security regulatory set. The only way assure compliancy is to implement a well-designed multi-level security strategy. This includes traditional technology solutions such as a network firewall perimeter and locally implemented firewalls, as well as email and security filtering. It also includes non-technical solutions as well. Examples include continual security awareness training for all personnel, as well as a carefully crafted and rehearsed Incident Response Plan. But if these customary solutions were enough by themselves, the world would be void of data breaches and other types of intrusive cyberattacks. In order to secure the access and integrity of information critical to the United States, you need a super defense weapon. PolicyPak is what you need to protect vulnerable desktop attach surfaces.
Management with PolicyPak Least Privilege Manager
The principle of least privilege is at the very essence of two of the security controls specified by NIST Special Publication 800-171:
- Access Control and Identification
- Authentication
Too often, companies today allocate local admin rights to (what should be) standard users. This not only provides overarching rights and privileges these users don’t need but gives potential admin rights and privileges to malicious software and code are downloaded or installed under these user accounts. This presents gaping holes in even the best-intentioned security strategy.
In the past, enterprise admins have been reluctant to deny local admin rights due to possible work disruptions. That is no longer the case with PolicyPak Least Privilege Manager. Because PolicyPak editors are built inside the Group Policy Management Editor, admins are already familiar with its policy creation process. All they need to do is make a policy for standard users and give them the granular rights they need to do things such run a windows installer application or run a script. The example below shows the creation of a new executable policy.

After creating the policy, you can then identify the given .exe file by its path, hash value, signature or file information, as shown in the figure below.

The same principle applies to Control Panel applets. Create a policy that assigns standard users full access to the exact Control Panel tool they need regardless of their default rights. In the example below, a user is being given access to Device Manager.

You can watch a video demonstration on our website showing how you can kill local admin rights for standard users once and for all.
NIST 800-171 Tip: Implementing a Solid Defense
The greatest defensive weapon in the PolicyPak security arsenal is SecureRunTM. Think of it as a blanket Allow List without the hassle. Its untrusting nature makes it ideal for any zero-trust strategy. It doesn’t trust the user, nor the files that the user is clicking on. It operates under the simple premise that when users download files off the Internet or copy them from a USB drive, they own the file and must be on a list of trusted users to be able to run it, as seen in the following screenshot.
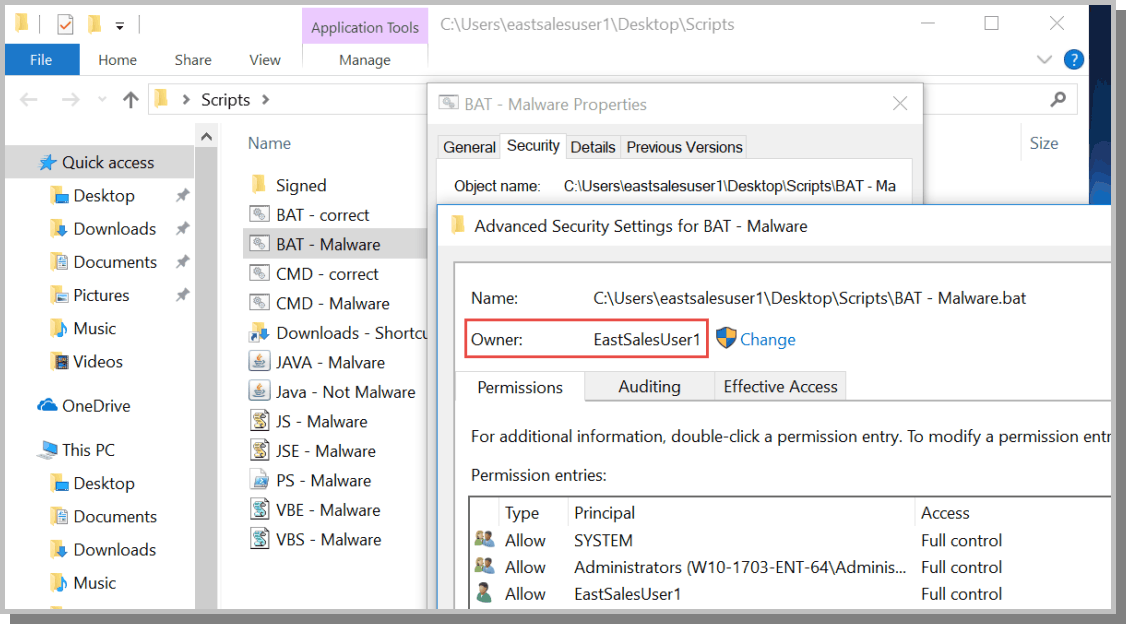
When SecureRun™ is on, PolicyPak Least Privilege Manager checks to see who owns the executable, MSI, script, or Java JAR file. SecureRun™ then maintains a list of who can initiate new processes. Below is an example of the default list, which you can modify to your needs.

A user that is not on the SecureRun™ Members list is not trusted, thus blocking processes originating from that user. The result is that properly installed applications can run perfectly well, but all unknown applications and scripts are blocked, as shown below in the following screenshot.

You can watch a video demonstration on our website on how to stop ransomware and unknown zero-day attacks with a few clicks of the mouse.
NIST 800-171 Tip: Configuration Management
One of the security controls outlined in NIST SP 800-171 is configuration management. In order to properly secure your network environment, you must have control over what protocols, services, and features are running on your desktops. For instance, hackers have been exploiting the SMBv1 protocol for years using malware attacks, crippling Fortune 500 enterprises throughout the world. PolicyPak Feature Manager gives you absolute control over the exact Windows features that reside on your desktops. All you need to do is create a policy and then add or remove Windows classic features and Windows 10 optional features according to your needs, as shown in the figure below. In doing so, you significantly reduce the attack surface of your desktops. By controlling your desktop environment, you control your security.
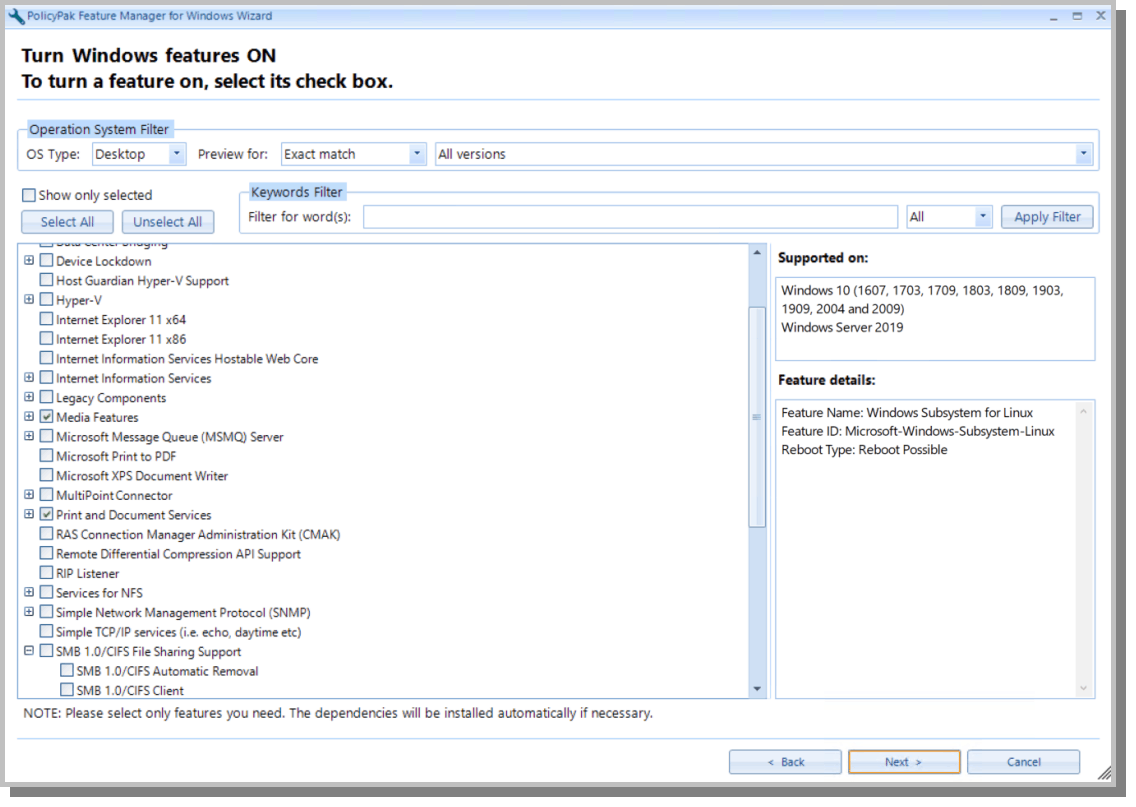
You can watch a video demonstration on our website on how you can dictate what protocols and features reside on all of your Windows desktops.
NIST 800-171 Tip: Security for Non-Domain-Joined Machines
While the PolicyPak solution set may utilize the Group Policy Editor, it is not limited to domain-joined computers. With PolicyPak MDM Edition, you can easily import any and all PolicyPak policies into your favorite MDM solution and deploy them to all enrolled Windows machines. With PolicyPak Cloud Edition, you can apply policies in real time to any Internet connected device anywhere in the world, including stand-alone machines. That’s because PolicyPak is built around the principle that all computers must be secured in the zero-trust world we operate in today.
NIST 800-171 Tip: Other Tools
PolicyPak offers a complete security solution set worthy of securing high-priority networks.
- With PolicyPak Remote Work Delivery Manager you can deploy software to any on-prem or remote work computer. This includes web services like Dropbox, Azure, S3, etc. You can even uninstall software once the assigned policy no longer applies. This ensures that each user gets the exact software they need in a secure fashion.
- With PolicyPak Applications Manager, you can configure and lockdown thousands of user settings on hundreds of commonly used applications including Firefox, Java, Flash, IE, and Adobe products.
- With PolicyPak Browser Router, you can guarantee that specific websites and Intranet/Internet applications operate exclusively in the most optimum and secure browser.
PolicyPak is All about Defense
PolicyPak has been defending enterprises of all sizes and industries for years and will continue to do so. Whether you need to protect data that’s imperative to national security, or information that is proprietary to your business or customers, PolicyPak has the solution set you need to secure and protect your desktop attack surface.


