Jeremy Moskowitz founded PolicyPak Software after working with hundreds of customers with the same problem they couldn’t manage their applications, browsers and operating systems using the technology they already utilized.

Secure Your Zoom Sessions (and prevent Zoom-bombing) with Group Policy and PolicyPak
The previous month has been a rollercoaster ride for Zoom. As companies rushed to send employees out the door to work from home and reduce their exposure to the global pandemic, companies turned to collaboration applications such as Zooms to conduct meetings as usual. Unfortunately, the spotlight on Zoom also attracted some nefarious players who focused their attention on possible vulnerabilities. Like all software, some known exploits were discovered.
Password Vulnerability
The most serious threat is credential compromise. Hackers have figured out a way to obtain passwords while attending a Zoom Session. The problem occurs within the chat feature. Currently, the Zoom client converts any Windows networking UNC path into a clickable link within the chat messages. When a user clicks a link to lets say a shared JPG file, Windows naturally attempts to connect to the remote site using the SMB file-sharing protocol. In doing this, Windows sends the user’s login name and NTLM password hash by default. The involved has can then be cracked using free cracking tools that are easily obtainable today. If the user is using a simple password, it can easily be cracked within seconds.
How Group Policy and PolicyPak Can Eliminate this Vulnerability
Even if Zoom comes out with a fix, there’s something you can do proactively.
Use a Group Policy Administrative Template setting which simply restricts outgoing NTLM traffic. Create a GPO and go to Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options and configure “Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers” to Deny All.
The problem is what about computers that are not domain-joined? Furthermore, what about users that are now working remotely from home and must connect to the corporate network through VPN to get the GP update? They don’t need to use VPN to run a remote Zoom session.
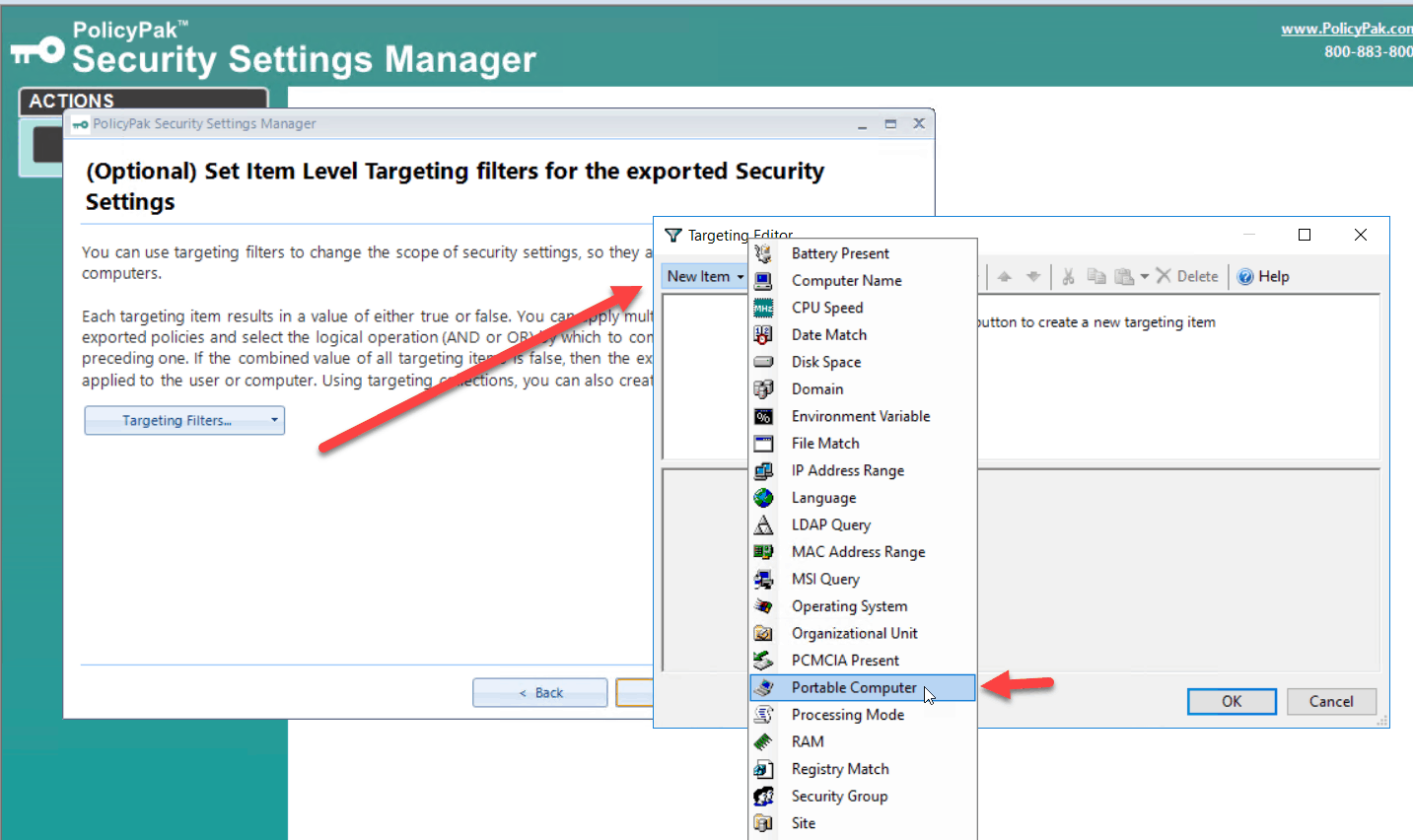
That’s where PolicyPak comes in. With PolicyPak Security Settings Manager you can configure Windows Security Settings using Real Group Policy and then export them into an XML file suing the PolicyPak Security Settings Manager export wizard.
PolicyPak Security Settings Manager simply analyzes your existing Windows Security settings. You can then decide which settings you want to export.
This probably isn’t a setting you want to deploy enterprise wide. Just to your laptop users or even selected ones. PolicyPak allows you to granularly target most any setting using Item-level Targeting. In this case, I am going to target portable computers you can also target a specific version of the Windows OS or a particular user group.
Finally, we will simply save file. You can then use PolicyPak Cloud Edition to deploy the new setting in rapid fashion to your remote machines whether they are domain joined or not. For MDM enrolled computers, you can use the PolicyPak Exporter Utility to convert the XML into a MSI file that you can then simply deploy through your preferred MDM using PolicyPak MDM Edition in the same way you deploy any MSI file.
Once the Zoom update is deployed throughout your enterprise, you can go back and disable this setting.
You can watch a video demonstration showing how you can deliver Group Policy Security settings over the internet.
Zoom-Bombing
Although not as serious, Zoom-bombing is a more prevalent threat. Just like photo bombing, it entails bombing someone’s Zoom meeting with unwanted images or videos. The FBI has even issued a warning about using Zoom as it has received multiple reports of conferences being disrupted by pornographic and/or hate images and threatening language. This warning is especially pertinent to schools.
Fortunately, there are some things you can to lessen your exposure to Zoom Bombing. The first is to refrain from publicizing your zoom meetings on the web or the company website. One can simply do a Google search for URLs that include “zoom.us”.
Some other tips you can take include:
- Enable the waiting room feature for all meetings so that you can see who is attempting to join a meeting before you allow them access
- Ensure that the Zoom option setting “Join before host” is set to its default “disabled” setting.
- Once a meeting starts, lock the meeting to prevent anyone else from joining
- If the host is the only one presenting, then mute the controls for all other participants
To get started with some of these recommendations, you can and should download the Zoom ADMX settings. Then, put them in your Central Store (here’s a video if you don’t know how to do that.)
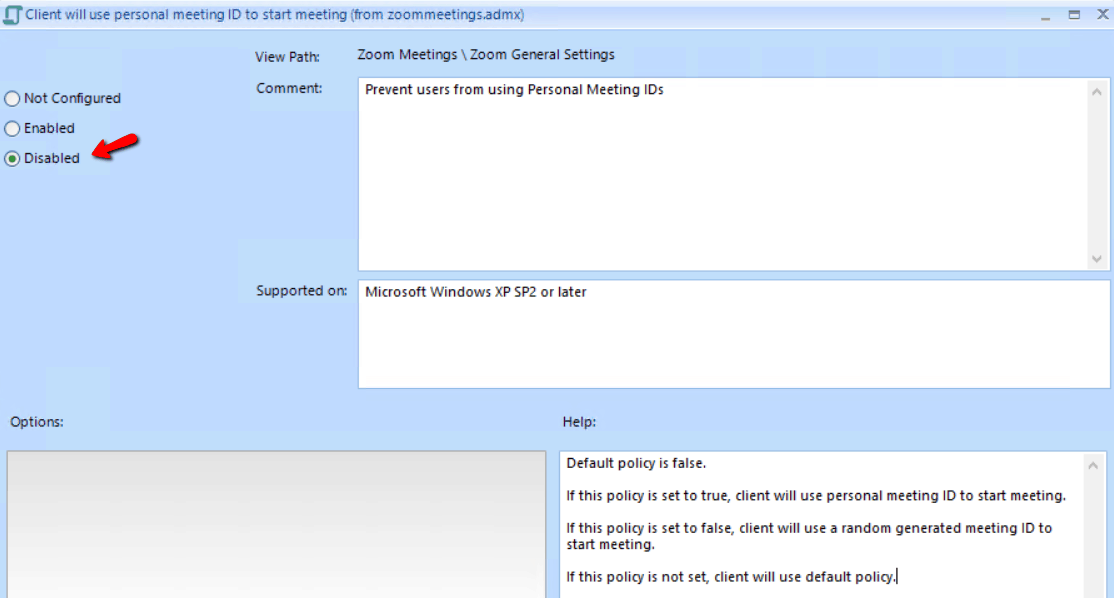
One of the recommendations from Zoom is to refrain from using your Personal Meeting ID and use a per-meeting ID that is exclusive to a single meeting. Do this by disabling the “AlwaysUsePersonalMeetingID” setting. The best way to deliver this setting would be via PolicyPak Admin Templates Manager.
PolicyPak Admin Templates Manager lets you configure any GP ADMX setting and deploy it both domain and non domain-joined computers (just as in our earlier example.)
Here is how the desired setting should look.
BONUS TIP: Zoom provides a video that walks you through the process of generating a random meeting ID.
If your company uses Zoom for intracompany meetings only, you can restrict access to your company’s email domain only.
You can watch a video demonstration showing how you can use PolicyPak to Group Policy Admin template settings over the internet via PolicyPak Cloud.
Summary
PolicyPak is a modern desktop management solution that empowers you to easily configure, deploy, and manage policies for on-premises and remote work Windows environments. Our suite of solutions allows you to completely manage and secure user desktops regardless of join status or location. Out solutions are ideally suited today for remote workspaces. PolicyPak also allows you to swiftly respond to discovered security vulnerabilities to shore up recently discovered vulnerabilities. Find out how PolicyPak is perfectly positioned for the challenges of today.